
Prevent account creation fraud with AWS WAF Fraud Control – Account Creation Fraud Prevention
Threat actors use sign-up pages and login pages to carry out account fraud, including taking unfair advantage of promotional and sign-up bonuses, publishing fake reviews, and spreading malware… In 2022, AWS released AWS WAF Fraud Control – Account Takeover Prevention (ATP) to help protect your…
Threat actors use sign-up pages and login pages to carry out account fraud, including taking unfair advantage of promotional and sign-up bonuses, publishing fake reviews, and spreading malware.
In 2022, AWS released AWS WAF Fraud Control – Account Takeover Prevention (ATP) to help protect your application’s login page against credential stuffing attacks, brute force attempts, and other anomalous login activities.
Today, we introduce AWS WAF Fraud Control – Account Creation Fraud Prevention (ACFP) to help protect your application’s sign-up pages against fake account creation by detecting and blocking fake account creation requests.
You can now get comprehensive account fraud prevention by combining AWS WAF Account Creation Fraud Prevention and Account Takeover Prevention in your AWS WAF web access control list (web ACL). In this post, we will show you how to set up AWS WAF with ACFP for your application sign-up pages.
Overview of Account Creation Fraud Prevention for AWS WAF
ACFP helps protect your account sign-up pages by continuously monitoring requests for anomalous digital activity and automatically blocking suspicious requests based on request identifiers, behavioral analysis, and machine learning.
ACFP uses multiple capabilities to help detect and block fake account creation requests at the network edge before they reach your application. An automated vetting process for account creation requests uses rules based on reputation and risk to protect your registration pages against use of stolen credentials and disposable email domains. ACFP uses silent challenges and CAPTCHA challenges to identify and respond to sophisticated bots that are designed to actively evade detection.
ACFP is an AWS Managed Rules rule group. If you already use AWS WAF, you can configure ACFP without making architectural changes. On a single configuration page, you specify the registration page request inspection parameters that ACFP uses to detect fake account creation requests, including user identity, address, and phone number.
ACFP uses session tokens to separate legitimate client sessions from those that are not. These tokens allow ACFP to verify that the client applications that sign up for an account are legitimate. The AWS WAF Javascript SDK automatically generates these tokens during the frontend application load. We recommend that you integrate the AWS WAF Javascript SDK into your application, particularly for single-page applications where you don’t want page refreshes.
Walkthrough
In this walkthrough, we will show you how to set up ACFP for AWS WAF to help protect your account sign-up pages against account creation fraud. This walkthrough has two main steps:
- Set up an AWS managed rule group for ACFP in the AWS WAF console.
- Add the AWS WAF JavaScript SDK to your application pages.
Set up Account Creation Fraud Prevention
The first step is to set up ACFP by creating a web ACL or editing an existing one. You will add the ACFP rule group to this web ACL.
The ACFP rule group requires that you provide your registration page path, account creation path, and optionally the sign-up request fields that map to user identity, address, and phone number. ACFP uses this configuration to detect fraudulent sign-up requests and then decide an appropriate action, including blocking, challenging interstitial during the frontend application load, or requiring a CAPTCHA.
To set up ACFP
- Open the AWS WAF console, and then do one of the following:
- To create a new web ACL, choose Create web ACL.
- To edit an existing web ACL, choose the name of the ACL.
- On the Rules tab, for the Add Rules dropdown, select Add managed rule groups.
- Add the Account creation fraud prevention rule set to the web ACL. Then, choose Edit to edit the rule configuration.
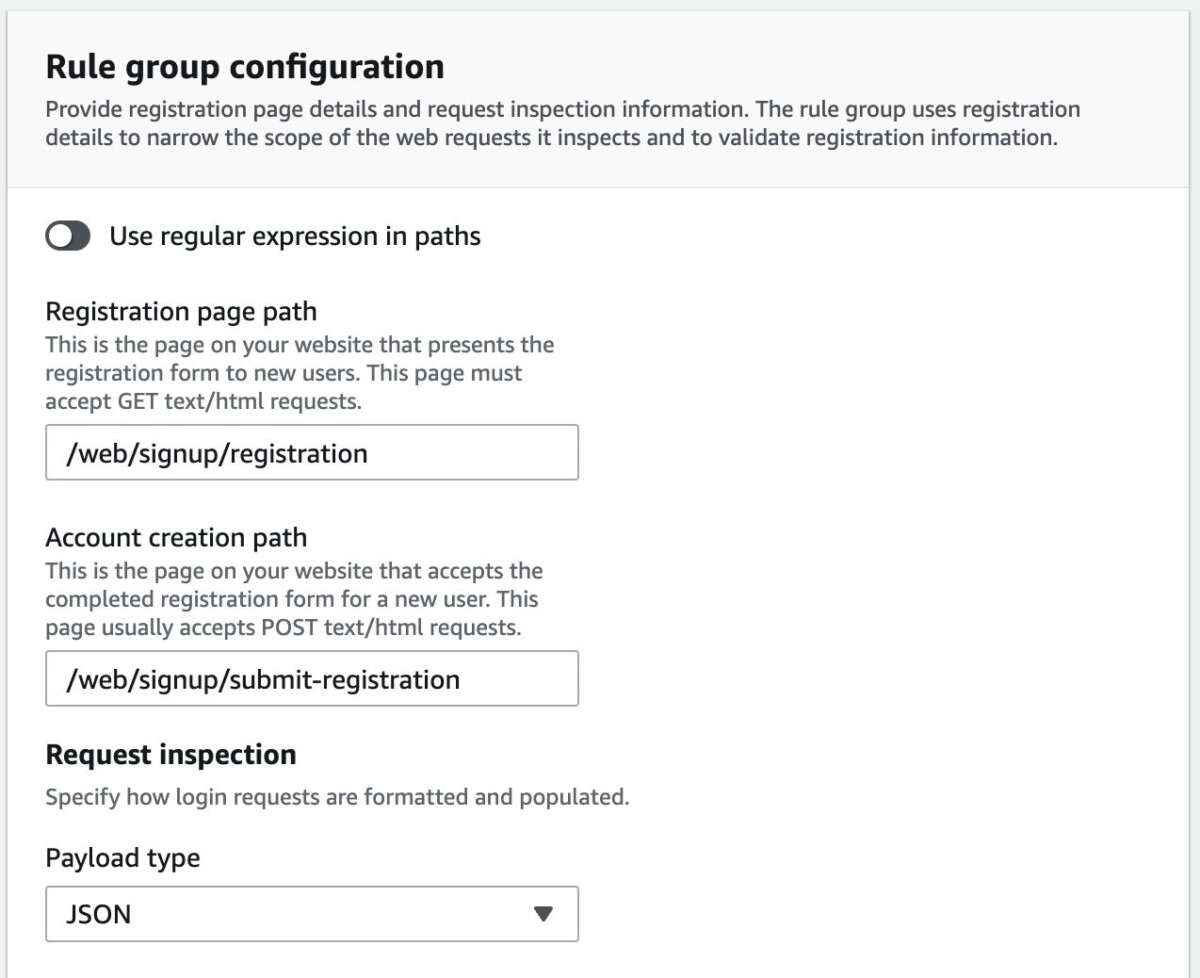
- For Rule group configuration, provide the following information that the ACFP rule group requires to inspect account creation requests, as shown in Figure 1.
- For Registration page path, enter the path for the registration page website for your application.
- For Account creation path, enter the path of the endpoint that accepts the completed registration form.
- For Request inspection, select whether the endpoint that you specified in Account creation path accepts JSON or FORM_ENCODED payload types.

Figure 1: Account creation fraud prevention – Add account creation paths
- (Optional): Provide Field names used in submitted registration forms, as shown in Figure 2. This helps ACFP more accurately identify requests that contain information that is considered stolen, or with a bad reputation. For each field, provide the relevant information that was included in your account creation request. For this walkthrough, we use JSON pointer syntax.

Figure 2: Account creation fraud prevention – Add optional field names
- For Account creation fraud prevention rules, review the actions taken on each category of account creation fraud, and optionally customize them for your web applications. For this walkthrough, we leave the default rule action for each category set to the default action, as shown in Figure 3. If you want to customize the rules, you can select different actions for each category based on your application security needs:
- Allow — Allows the request to be sent to the protected resource.
- Block — Blocks the request, returning an HTTP 403 (Forbidden) response.
- Count — Allows the request to be sent to the protected resource while counting detections. The count shows you bot activity that is occurring without blocking or challenging. When you turn on rules for the first time, this information can help you see what the detections are, before you change the actions.
- CAPTCHA and Challenge — use CAPTCHA puzzles and silent challenges with tokens to track successful client responses.

Figure 3: Account creation fraud prevention – Select actions for each category
- To save the configuration, choose Save.
- To add the ACFP rule group to your web ACL, choose Add rules.
- (Optional) Include additional rules in your web ACL, as described in the Best practices section that follows.
- To create or edit your web ACL, proceed through the remaining configuration pages.
Add the AWS WAF JavaScript SDK to your application pages
The next step is to find the AWS WAF JavaScript SDK and add it to your application pages.
The SDK injects a token in the requests that you send to your protected resources. You must use the SDK integration to fully enable ACFP detections.
To add the SDK to your application pages
- In the AWS WAF console, in the left navigation pane, choose Application integration.
- Under Web ACLs that are enabled for application integration, choose the name of the web ACL that you created previously.
- Under JavaScript SDK, copy the provided code snippet. This code snippet allows for creation of the cryptographic token in the background when the application loads for the first time. Figure 4 shows the SDK link.

Figure 4: Application integration – Add JavaScript SDK link to application pages
- Add the code snippet to your pages. For example, paste the provided script code within the
<head>section of the HTML. For ACFP, you only need to add the code snippet to the registration page, but if you are using other AWS WAF managed rules such as Account Takeover Protection or Targeted Bots on other pages, you will also need to add the code snippet to those pages. - To validate that your application obtains tokens correctly, load your application in a browser and verify that a cookie named
aws-waf-tokenhas been set during page load.
Review metrics
Now that you’ve set up the web ACL and integrated the SDK with the application, you can use the bot visualization dashboard in AWS WAF to review fraudulent account creation traffic patterns. ACFP rules emit metrics that correspond to their labels, helping you identify which rule within the ACFP rule group initiated an action. You can also use labels and rule actions to filter AWS WAF logs so that you can further examine a request.
To view AWS WAF metrics for the distribution
- In the AWS WAF console, in the left navigation pane, select Web ACLs.
- Select the web ACL for which ACFP is enabled, and then choose the Bot Control tab to view the metrics.
- In the Filter metrics by dropdown, select Account creation fraud prevention to see the ACFP metrics for your web ACL.

Figure 5: Account creation fraud prevention – Review web ACL metrics
Best practices
In this section, we share best practices for your ACFP rule group setup.
Limit the requests that ACFP evaluates to help lower costs
ACFP evaluates web ACL rules in priority order and takes the action associated with the first rule that a request matches. Requests that match and are blocked by a rule will not be evaluated against lower priority rules. ACFP only evaluates an ACFP rule group if a request matches the registration and account creation URI paths that are specified in the configuration.
You will incur additional fees for requests that ACFP evaluates. To help reduce ACFP costs, use higher priority rules to block requests before the ACFP rule group evaluates them. For example, you can add a higher priority AWS Managed Rules IP reputation rule group to block account creation requests from bots and other threats before ACFP evaluates them. Rate-based rules with a higher priority than the ACFP rule group can help mitigate volumetric account creation attempts by limiting the number of requests that a single IP can make in a five-minute period. For further guidance on rate-based rules, see The three most important AWS WAF rate-based rules.
If you are using the AWS WAF Bot Control rule group, give it a higher priority than the ACFP rule group because it’s less expensive to evaluate.
Use SDK integration
ACFP requires the tokens that the SDK generates. The SDK can generate these tokens silently rather than requiring a redirect or CAPTCHA. Both AWS WAF Bot Control and AWS WAF Fraud Control use the same SDK if both rule groups are in the same web ACL.
These tokens have a default immunity time (otherwise knowns as a timeout) of 5 minutes, after which AWS WAF requires the client to be challenged again. You can use the AWS WAF integration fetch wrapper in your single-pane application to help ensure that the token retrieval completes before the client sends requests to your account creation API without requiring a page refresh. Alternatively, you can use the getToken operation if you are not using fetch.
You can continue to use the CAPTCHA JavaScript API instead if you’ve already integrated this into your application.
Use both ACFP and ATP for comprehensive account fraud prevention
You can help prevent account fraud for both sign-up and login pages by enabling the ATP rule group in the same web ACL as ACFP.
Test ACFP before you deploy it to production
Test and tune your ACFP implementation in a staging or testing environment to help avoid negatively impacting legitimate users. We recommend that you start by deploying your rules in count mode in production to understand potential impact to your traffic before switching them back to the default rule actions. Use the default ACFP rule group actions when you deploy the web ACL to production. For further guidance, see Testing and Deploying ACFP.
Pricing and availability
ACFP is available today on Amazon CloudFront and in 22 AWS Regions. For information on availability and pricing, see AWS WAF Pricing.
Conclusion
In this post, we showed you how to use ACFP to protect your application’s sign-up pages against fake account creation. You can now combine ACFP with ATP managed rules in a single web ACL for comprehensive account fraud prevention. For more information and to get started today, see the AWS WAF Developer Guide.
If you have feedback about this post, submit comments in the Comments section below. If you have questions about this post, start a new thread on the AWS Security, Identity, & Compliance re:Post or contact AWS Support.
Want more AWS Security news? Follow us on Twitter.
Author: David MacDonald




