
Validate IAM policies with Access Analyzer using AWS Config rules
git clone https://github… In this post, you learn how to set up and continuously validate and report on compliance of the IAM policies in your environment using AWS Config… AWS Config evaluates the configuration settings of your AWS resources with the help of AWS Config rules, which r…
You can use AWS Identity and Access Management (IAM) Access Analyzer policy validation to validate IAM policies against IAM policy grammar and best practices. The findings generated by Access Analyzer policy validation include errors, security warnings, general warnings, and suggestions for your policy. These findings provide actionable recommendations that help you author policies that are functional and conform to security best practices.
You can use the IAM Policy Validator for AWS CloudFormation and the IAM Policy Validator for Terraform solutions to integrate Access Analyzer policy validation in a proactive manner within your continuous integration and continuous delivery CI/CD pipeline before deploying IAM policies to your Amazon Web Service (AWS) environment. Customers requested a similar capability to validate policies already deployed within their environments as part of the defense-in-depth strategy.
In this post, you learn how to set up and continuously validate and report on compliance of the IAM policies in your environment using AWS Config. AWS Config evaluates the configuration settings of your AWS resources with the help of AWS Config rules, which represent your ideal configuration settings. AWS Config continuously tracks the configuration changes that occur among your resources and checks whether these changes conform to the conditions in your rules. If a resource doesn’t conform to a rule, AWS Config flags the resource and the rule as noncompliant.
You can use this solution to validate identity-based and resource-based IAM policies attached to resources in your AWS environment that might have grammatical or syntactical errors or might not follow AWS best practices. The code used in this post is hosted in a GitHub repository.
Prerequisites
Before you get started, you need:
- An AWS account
- Basic knowledge of AWS Config, AWS CloudFormation and Amazon Simple Storage Service
- AWS Command Line Interface (AWS CLI) installed
- An Amazon S3 bucket
Step 1: Enable AWS Config to monitor global resources
To get started, enable AWS Config in your AWS account by following the instructions in the AWS Config Developer Guide.
Next, enable the recording of global resources:
- Open the AWS Management Console and go to the AWS Config console.
- Go to Settings and choose Edit to see the AWS Config recorder settings.
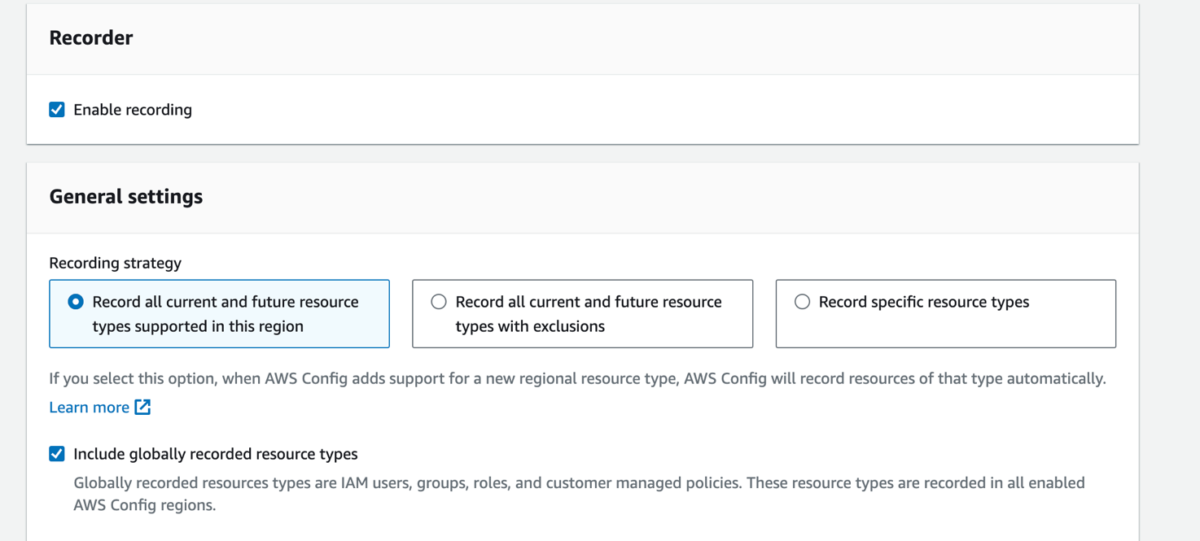
- Under General settings, select the Include globally recorded resource types to enable AWS Config to monitor IAM configuration items.
- Leave the other settings at their defaults.
- Choose Save.

Figure 1: AWS Config settings page showing inclusion of globally recorded resource types
- After choosing Save, you should see Recording is on at the top of the window.

Figure 2: AWS Config settings page showing recorder settings
Note: You only need to enable globally recorded resource types in the AWS Region where you’ve configured AWS Config because they aren’t tied to a specific Region and can be used in other Regions. The globally recorded resource types that AWS Config supports are IAM users, groups, roles, and customer managed policies.
Step 2: Deploy the CloudFormation template
In this section, you deploy and test a sample AWS CloudFormation template that creates the following:
- An AWS Config rule that reports the compliance of IAM policies.
- An AWS Lambda function that implements and then makes the requests to IAM Access Analyzer and returns the policy validation findings.
- An IAM role that’s used by the Lambda function with permissions to validate IAM policies using the Access Analyzer ValidatePolicy API.
- An optional Amazon CloudWatch alarm and Amazon Simple Notification Service (Amazon SNS) topic to provide notification of Lambda function errors.
Follow the steps below to deploy the AWS CloudFormation template:
- To deploy the CloudFormation template using the following command, you must have the AWS Command Line Interface (AWS CLI) installed.
- Make sure you have configured your AWS CLI credentials.
- Clone the solution repository.
- Navigate to the iam-access-analyzer-config-rule folder of the cloned repository.
- Deploy the CloudFormation template using the AWS CLI.
Note: Change the Region for the parameter — RegionToValidateGlobalResources — to the Region you enabled for global resources in Step 1. Optionally, you can add an email address if you want to receive notifications if the AWS Config rule stops working. Use the code that follows, replacing <us-east-1> with the Region you enabled and <EMAIL_ADDRESS> with your chosen address.
- After successful deployment, you will see the message Successfully created/updated stack – iam-policy-validation-config-rule.

Figure 3: Successful CloudFormation stack creation reported on the terminal
Note: If the CloudFormation stack creation fails, go to the CloudFormation console and select the iam-policy-validation-config-rule stack. Choose Events to review the failure reason.
- After deployment, open the CloudFormation console and select the iam-policy-validation-config-rule stack.
- Choose Resources to see the resources created by the template.
Step 3: Check noncompliant resources discovered by AWS Config
The AWS Config rule is designed to mark resources that have IAM policies as noncompliant if the resources have validation findings found using the IAM Access Analyzer ValidatePolicy API.
- Open the AWS Config console
- Choose Rules from the navigation pane on the left and select policy-validation-config-rule.

Figure 4: AWS Config rules page showing the rule details
- Scroll down on the page and filter Resources in Scope to see the noncompliant resources.

Figure 5: AWS Config rules page showing noncompliant resources
Note: If the AWS Config rule isn’t invoked yet, you can choose Actions and select Re-evaluate to invoke it.

Figure 6: AWS Config rules page showing evaluation invocation
Step 4: Modify the AWS Config rule for exceptions
You might want to exempt certain resources from specific policy validation checks. For example, you might need to deploy a more privileged role—such as an administrator role—to your environment and you don’t want that role’s policies to have policy validation findings.

Figure 7: AWS Config rules page showing a noncompliant administrator role
This section shows you how to configure an exceptions file to exempt specific resources.
- Start by configuring an exceptions file similar to the one that follows to log general warning findings across the accounts in your organization to make sure your policies conform to best practices by setting ignoreWarningFindings to False.
- Additionally, you might want to create an exception that allows administrator roles to use the iam:PassRole action on another role. This combination of action and resource is usually reserved for privileged users. The example file below shows an exception for all the roles created with Administrator in the role path from account 12345678912.
Example exceptions file:
{ "global":{ "ignoreWarningFindings":false }, "12345678912":{ "ignoreFindingsWith":[ { "issueCode":"PASS_ROLE_WITH_STAR_IN_ACTION_AND_RESOURCE", "resourceType":"AWS::IAM::Role", "resourceName":"Administrator/*" } ] } } - After the exceptions file is ready, upload the JSON file to the S3 bucket you created as a part of the prerequisites.
You can manage this exceptions file by hosting it in a central Git repository. When teams need to exempt a particular resource from these policy validation checks, they can submit a pull request to the central repository. An approver can then approve or reject this request and, if approved, deploy the updated exceptions file.
- Modify the bucket policy so that the bucket is accessible to your AWS Config rule if the rule is operating in a different account than the bucket was created in. Below is an example of a bucket policy that allows the accounts in your organization to read the exceptions file.
Note: For more examples visit example policy validation exceptions file contents.
- Deploy the CloudFormation template again using the ExceptionsS3BucketName and ExceptionsS3FilePrefix parameters. The file prefix should be the full prefix of the S3 object exceptions file.
- After you see the Successfully created/updated stack – iam-policy-validation-config-rule message on the terminal or command line and the AWS Config rule has been re-evaluated, the resources mentioned in the exception file should show as Compliant.

Figure 8: Resource exception result
You can find additional customization options in the exceptions file schema.
Cleanup
To avoid recurring charges and to remove the resources used in testing the solution outlined in this post, use the CloudFormation console to delete the iam-policy-validation-config-rule CloudFormation stack.

Figure 9: AWS CloudFormation stack deletion
Conclusion
In this post, we demonstrated how you can set up a centralized compliance and monitoring workflow using AWS IAM Access Analyzer policy validation with AWS Config rules to validate identity-based and resource-based policies attached to resources in your account. Using this solution, you can create a single pane of glass to monitor resources and govern centralized compliance for AWS Config-supported resources across accounts. You can also build and maintain exceptions customized to your environment as shown in the example policy validation exceptions file. You can visit the Access Analyzer policy checks reference page for a complete list of policy check validation errors and resolutions.
If you have feedback about this post, submit comments in the Comments section below. If you have questions about this post, contact AWS Support.
Want more AWS Security news? Follow us on Twitter.
Author: Anurag Jain







