
AWS Network Firewall Geographic IP Filtering launch
In this blog post, we discuss Geographic IP Filtering, a new feature of Network Firewall that you can use to filter traffic based on geographic location and meet compliance requirements… This includes restricting traffic to and from their workloads in Amazon Web Services (AWS) to certain geograph…
AWS Network Firewall is a managed service that provides a convenient way to deploy essential network protections for your virtual private clouds (VPCs). In this blog post, we discuss Geographic IP Filtering, a new feature of Network Firewall that you can use to filter traffic based on geographic location and meet compliance requirements.
Customers with internet-facing applications are constantly in need of advanced security features to protect their applications from threat actors. This includes restricting traffic to and from their workloads in Amazon Web Services (AWS) to certain geographies because of security risk. Customers operating in highly regulated industries—such as banking, public sector, or insurance—might have specific security requirements that can be addressed by Geographic IP Filtering.
Previously, customers had to rely on third-party tools for retrieving an IP address list of specific countries and updating their firewall rules on a regular basis to meet applicable requirements. Now, with Geographic IP Filtering on Network Firewall, you can protect your application workloads based on the geolocation of the IP address. As new IP addresses are assigned by the Internet Assigned Numbers Authority (IANA), the Geographic IP database underneath Network Firewall is automatically updated so that the service can consistently filter inbound and outbound traffic from specific countries based on country codes. It supports IPv4 and IPv6 traffic.
Geographic IP Filtering is supported in all AWS Regions where Network Firewall is available today, including the AWS GovCloud (US) Regions.
Set up Geographic IP Filtering in Network Firewall
You can use Network Firewall to inspect network traffic and protect your VPCs using layer 3–7 rules (network layer to application layer of the OSI model). When traffic reaches Network Firewall, it will identify the location of the source and destination IP address from the Geographic IP database and block traffic if you have a firewall rule to block that location. You can choose to pass, drop, reject, or create an alert for traffic coming from or going to specific countries.
Before setting up Geographic IP Filtering rules, you need to deploy Network Firewall and attach a firewall policy. You can learn more about these steps in the Network Firewall Getting Started guide. You can configure Network Firewall Geographic IP Filtering in minutes using the AWS Management Console, AWS Command Line Interface (AWS CLI), AWS SDK, or the Network Firewall API.
To configure Geographic IP Filtering rules using the console:
- Sign in to the AWS Management Console and open the Amazon VPC console.
- In the navigation pane, under Network Firewall, choose Network Firewall rule groups.
- Choose Create rule group.
- In the Create rule group page, for the Rule group type, select Stateful rule group.
- For the Rule group format, select Standard stateful rule.
- For Rule evaluation order, select either Strict order (recommended) or Action order.
- Enter a name for the stateful rule group.
- For Capacity, enter the maximum capacity you want to allow for the stateful rule group.
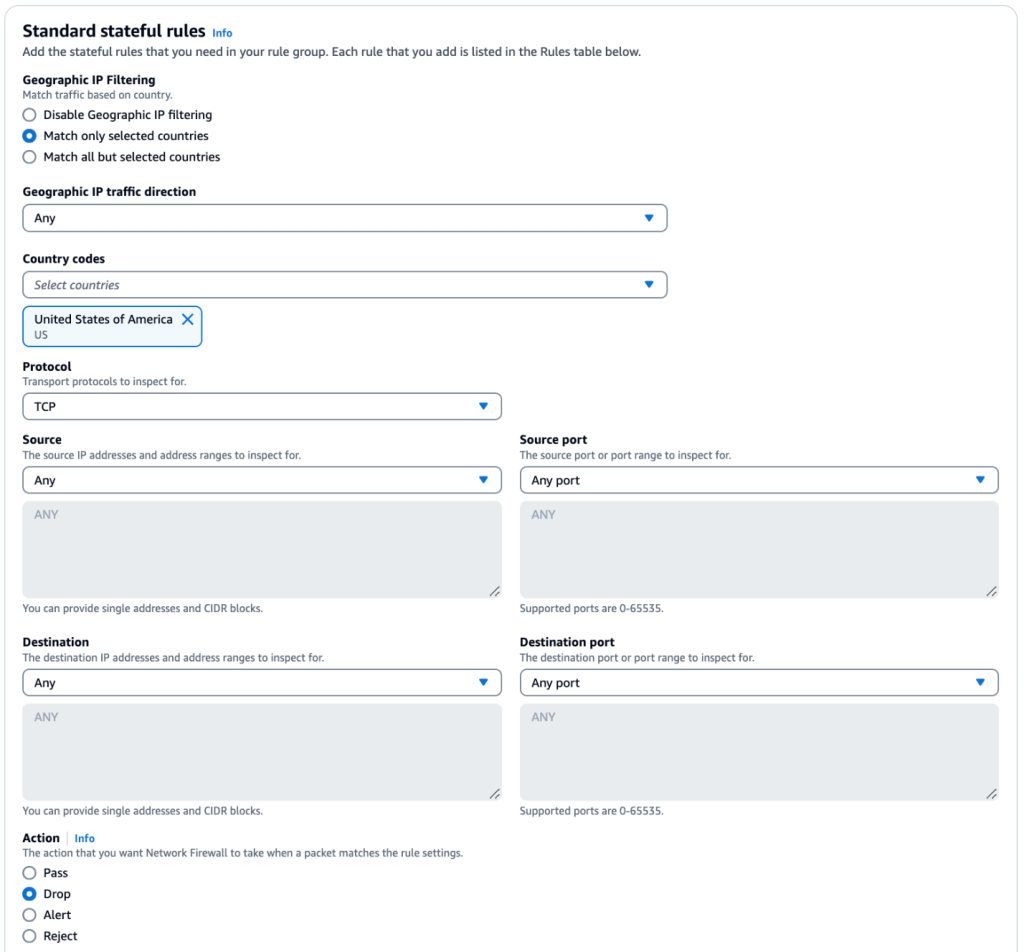
- Under Standard stateful rules, for Geographic IP Filtering, select whether you want to Disable Geographic IP filtering, Match only selected countries, or Match all but selected countries.
- If you opt for Geographic IP Filtering, then select the Geographic IP traffic direction and Country codes that you want to filter the traffic for.
- Enter the appropriate values for Protocol, Source, Source port, Destination, and Destination port.
- For Action, select the action that you want Network Firewall to take when a packet matches the rule settings.

Figure 1: Standard stateful rule
- Click Add rule and then review the rule to create the rule group.

Figure 2: Geographic IP Filtering rules
Suricata compatibility
You can also use Geographic IP filtering with Suricata-compatible rule strings using the geoip keyword.
To create a Suricata compatible rule string:
- Follow steps 1 through 4 of the previous procedure.
- For the Rule group format, select Suricata compatible rule string.
- For Rule evaluation order, select either Strict order (recommended) or Action order.
- Enter a name for the stateful rule group.
- For Capacity, enter the maximum capacity you want to allow for the stateful rule group.
- Under Suricata compatible rule string, enter an appropriate string based on your source and destination along with the country code to filter traffic for. To use a Geographic IP filter, provide the geoip keyword, the filter type, and the country codes for the countries that you want to filter for.
- Suricata supports filtering for source and destination IPs. You can filter on either of these types by itself, by specifying
dstorsrc. You can filter on the two types together with AND or OR logic, by specifyingbothorany.
For example, the following sample Suricata rule string drops traffic originating from Japan:
Note that Suricata determines the location of requests using MaxMind GeoIP databases. MaxMind reports very high accuracy of their data at the country level, although accuracy varies according to factors such as country and type of IP. For more information about MaxMind, see MaxMind IP Geolocation.
If you think any of the Geographic IP data is incorrect, you can submit a correction request to MaxMind at MaxMind Correct GeoIP Data.
Logging Geographic IP Filtering
You can configure Network Firewall logging for your firewall’s stateful engine to get detailed information about the packet and any stateful rule action taken against the packet. There are no changes to the logging and monitoring mechanism with the introduction of the Geographic IP Filtering feature. However, by explicitly specifying the msg and metadata keywords, you can see additional geographic information in the alert logs that can help with troubleshooting. If these keywords aren’t specified in the Suricata rule string, the log event will not show any geographic information.
Suricata rule examples
In this section, you will find examples of Suricata rule strings to pass, block, reject, and alert on traffic to or from a specific country.
Example 1: To pass ingress traffic from a specific country
The following example passes ingress traffic from India.
Note: The rule evaluation order should be set to
Strictfor alert logs to be generated in this example. If the rule evaluation order is set toAction, then although the traffic will pass, alert logs will not be generated.
The following are the alert and flow logs for Example 1.
Alert logs:
Flow logs from source to destination:
Flow logs from destination to source:
Example 2: To block ingress traffic from a specific country
The following example blocks ingress traffic from Japan.
Example 3: To block ingress SSH traffic from a specific country
The following example blocks ingress SSH traffic from Russia.
Example 4: To reject egress TCP traffic to a specific country:
The following example rejects egress TCP traffic to Iran.
Example 5: To alert on traffic originating from or destined to specific country
The following example alerts on traffic that originates from Venezuela.
Conclusion
You can use the new Geographic IP Filtering feature in AWS Network Firewall to enhance your security posture by controlling traffic based on geographic locations. In this post, you learned about the key concepts, configuration steps, and examples for implementing the Geographic IP Filtering feature in Network Firewall. By using this feature, businesses can protect their networks from potentially harmful traffic and control which geographic locations can interact with their infrastructure. As cyber threats continue to evolve, the Geographic IP Filtering feature serves as a vital tool for strengthening network security.
If you have feedback about this post, submit comments in the Comments section below. If you have questions about this post, contact AWS Support.
Author: Prasanjit Tiwari


