
A phased approach towards a complex HITRUST r2 validated assessment
Health Information Trust Alliance (HITRUST) offers healthcare organizations a comprehensive and standardized approach to information security, privacy, and compliance… HITRUST Common Security Framework (HITRUST CSF) can be used by organizations to establish a robust security program, ensure patien…
Health Information Trust Alliance (HITRUST) offers healthcare organizations a comprehensive and standardized approach to information security, privacy, and compliance. HITRUST Common Security Framework (HITRUST CSF) can be used by organizations to establish a robust security program, ensure patient data privacy, and assist with compliance with industry regulations. HITRUST CSF enhances security, streamlines compliance efforts, reduces risk, and contributes to overall security resiliency and the trustworthiness of healthcare entities in an increasingly challenging cybersecurity landscape.
While HITRUST primarily focuses on the healthcare industry, its framework and certification program are adaptable and applicable to other industries. The HITRUST CSF is a set of controls and requirements that organizations must comply with to achieve HITRUST certification. The HITRUST R2 assessment is the process by which organizations are evaluated against the requirements of the HITRUST CSF. During the assessment, an independent third party assessor examines the organization’s technical security controls, operational policies and procedures, and the implementation of all controls to determine if they meet the specified HITRUST requirements.
HITRUST r2 validated assessment certification is a comprehensive process that involves meeting numerous assessment requirements. The number of requirements can vary significantly, ranging from 500 to 2,000 depending on your environment’s risk factors and regulatory requirements. Attempting to address all of these requirements simultaneously especially when migrating systems to Amazon Web Services (AWS) can be overwhelming. By using a strategy of separating your compliance journey into environments and applications, you can streamline the process and achieve HITRUST compliance more efficiently and within a realistic timeframe.
In this blog post, we start by exploring the HITRUST domain structure, highlighting the security objective of each domain. We then show how you can use AWS configurable services to help meet these objectives.
Lastly, we present a simple and practical reference architecture with an AWS multi-account implementation that you can use as the foundation for hosting your AWS application, highlighting the phased approach for HITRUST compliance. Please note that this blog is intended to assist with using AWS services in a manner that supports an organization’s HITRUST compliance, but a HITRUST assessment is at an organizational level and involves controls that extend beyond the organization’s use of AWS.
HITRUST certification journey – Scope applications systems on AWS infrastructure:
The HITRUST controls needed for certification are structured within 19 HITRUST domains, covering a wide range of technical and administrative control requirements. To efficiently manage the scope of your certification assessment, start by focusing on the AWS landing zone, which serves as a critical foundational infrastructure component for running applications. When establishing the AWS landing zone, verify that it aligns with the AWS HITRUST security control requirements that are dependent on the scope of your assessment. Note that these 19 domains are a combination of technical controls and foundational administrative controls.
After you’ve set up a HITRUST compliant landing zone, you can begin evaluating your applications for HITRUST compliance as you migrate them to AWS. When you expand and migrate applications to the HITRUST-certified AWS landing zone assessed by your third party assessor, you can inherit the HITRUST controls required for application assessment directly from the landing zone. This simplifies and narrows the scope of your assessment activities.
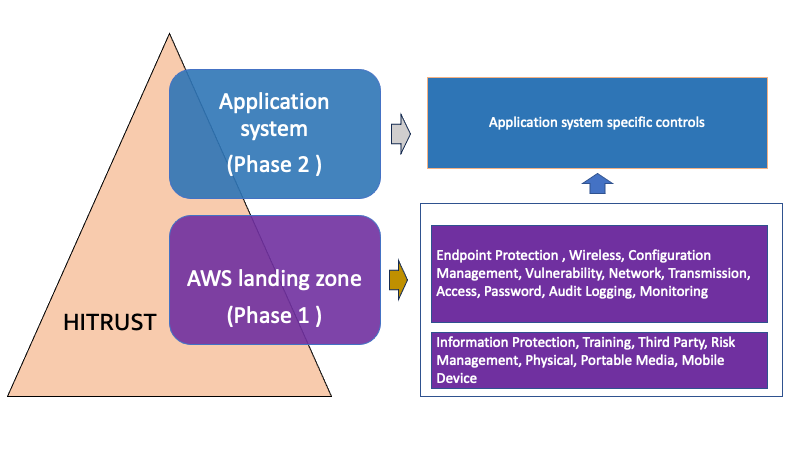
Figure 1 that follows shows the two key phases and how a bottom-up phased approach can be structured with related HITRUST controls.

Figure 1: HITRUST Phase 1 and Phase 2 high-level components
The diagram illustrates:
- An AWS landing zone environment as Phase 1 and its related HITRUST domain controls
- An application system as Phase 2 and its related application system specific controls
HITRUST domain security objectives:
The HITRUST CSF based certification consists of 19 domains, which are broad categories that encompass various aspects of information security and privacy controls. These domains serve as a framework for your organization to assess and enhance its security posture. These domains cover a wide range of controls and practices related to information security, privacy, risk management, and compliance. Each domain consists of a set of control objectives and requirements that your organization must meet to achieve HITRUST certification.
The following table lists each domain, the key security objectives expected, and the AWS configurable services relevant to the security objectives. These are listed as a reference to give you an idea of the scope of each domain; the actual services and tools to meet specific HITRUST requirements will vary depending upon your scope and its HITRUST requirements.
Note: The information in this post is a general guideline and recommendation based on a phased approach for HITRUST r2 validated assessment. The examples are based on the information available at the time of publication and are not a full solution.
HITRUST domains, security objectives, and related AWS services | ||
| HITRUST domain | Summary of key security objectives expected in HITRUST domains | Related AWS configurable services |
| 1. Information Protection Program |
| AWS Artifact AWS Service Catalog AWS Config Amazon Cybersecurity Awareness Training |
| 2. Endpoint Protection |
| AWS Systems Manager AWS Config Amazon Inspector AWS Shield AWS WAF |
| 3. Portable Media Security |
| AWS Identity and Access Management (IAM) Amazon Simple Storage Service (Amazon S3) AWS Key Management Service (AWS KMS) AWS CloudTrail Amazon Macie Amazon Cognito Amazon Workspaces Family |
| 4. Mobile Device Security |
| AWS Database Migration Service (AWS DMS) AWS IoT Device Defender AWS Snowball AWS Config |
| 5. Wireless Security |
| AWS Certificate Manager (ACM) |
| 6. Configuration Management |
| AWS Config AWS Trusted Advisor Amazon CloudWatch AWS Security Hub Systems Manager |
| 7. Vulnerability Management |
| Amazon Inspector CloudWatch Security Hub |
| 8. Network Protection |
| Amazon Route 53 AWS Control Tower Amazon Virtual Private Cloud (Amazon VPC) AWS Transit Gateway Network Load Balancer AWS Direct Connect AWS Site-to-Site VPN AWS CloudFormation AWS WAF ACM |
| 9. Transmission Protection |
| Systems Manager ACM |
| 10. Password Management |
| AWS Secrets Manager, Systems Manager Parameter Store, AWS KMS |
| 11. Access Control |
| IAM AWS Resource Access Manager (AWS RAM) Amazon GuardDuty AWS Identity Center |
| 12. Audit Logging & Monitoring |
| AWS Control Tower Amazon S3 CloudTrail GuardDuty AWS Config CloudWatch Amazon VPC Flow logs Amazon OpenSearch Service |
| 13. Education, Training and Awareness |
| Security Hub Amazon Cybersecurity Awareness Training Trusted Advisor |
| 14. Third-Party Assurance |
| AWS Artifact AWS Service Organization Controls (SOC) Reports ISO27001 reports |
| 15. Incident Management |
| AWS Incident Detection and Response Security Hub Amazon Inspector CloudTrail AWS Config Amazon Simple Notification Service (Amazon SNS) GuardDuty AWS WAF Shield CloudFormation |
| 16. Business Continuity & Disaster Recovery |
| AWS Backup & Restore CloudFormation Amazon Aurora CrossRegion replication AWS Backup Disaster Recovery: Pilot Light, Warm Standby, Multi Site Active-Active |
| 17. Risk Management |
| Trusted Advisor AWS Config Rules |
| 18. Physical & Environmental Security |
| AWS Data Centers Amazon CloudFront AWS Regions and Global Infrastructure |
| 19. Data Protection & Privacy |
| Amazon S3 AWS KMS Aurora OpenSearch Service AWS Artifact Macie |
Note: You can use AWS HITRUST-certified services to support your HITRUST compliance requirements. Use of these services in their default state doesn’t automatically ensure HITRUST certifiability. You must demonstrate compliance through formal formulation of policies, procedures, and implementation tailored to your scope, which involves configuring and customizing AWS HITRUST certified services to align precisely with HITRUST requirements within your scope and involves implementation of controls outside of the scope of the use of AWS services (such as appropriate organization-wide policies and procedures).
HITRUST phased approach – Reference architecture:
Figure 2 shows the recommended HITRUST Phase 1 and Phase 2 accounts and components within a landing zone.

Figure 2: HITRUST Phases 1 and 2 architecture including accounts and components
The reference architecture shown in Figure 2 illustrates:
- A high-level structure of AWS accounts arranged in HITRUST Phase 1 and Phase 2
- The accounts in HITRUST Phase 1 include:
- Management account: The management account in the AWS landing zone is the primary account responsible for governing and managing the entire AWS environment.
- Security account: The security account is dedicated to security and compliance functions, providing a centralized location for security-related tools and monitoring.
- Central logging account: This account is designed for centralized logging and storage of logs from all other accounts, aiding in security analysis and troubleshooting.
- Central audit: The central audit account is used for compliance monitoring, logging audit events, and verifying adherence to security standards.
- DevOps account: DevOps accounts are used for software development and deployment, enabling continuous integration and delivery (CI/CD) processes.
- Networking account: Networking accounts focus on network management, configuration, and monitoring to support reliable connectivity within the AWS environment.
- DevSecOps account: DevSecOps accounts combine development, security, and operations to embed security practices throughout the software development lifecycle.
- Shared services account: Shared services accounts host common resources, such as IAM services, that are shared across other accounts for centralized management.
The account group for HITRUST Phase 2 includes:
- Tenant A – sample application workloads
- Tenant B – sample application workloads
HITRUST Phase 1 – HITRUST foundational landing zone assessment phase:
In this phase you define the scope of assessment, including the specific AWS landing zone components and configurations that must be HITRUST compliant. The primary focus here is to evaluate the foundational infrastructure’s compliance with HITRUST controls. This involves a comprehensive review of policies and procedures, and implementation of all requirements within the landing zone scope. Assessing this phase separately enables you to verify that your foundational infrastructure adheres to HITRUST controls. Some of the policies, procedures, and configurations that are HITRUST assessed in this phase can be inherited across multiple applications’ assessments in later phases. Assessing this infrastructure once and then inheriting these controls for applications can be more efficient than assessing each application individually.
By establishing a secure and compliant foundation at the start, you can plan application assessments in later phases, making it simpler for subsequent applications to adhere to HITRUST requirements. This can streamline the compliance process and reduce the overall time and effort required. By assessing the landing zone separately, you can identify and address compliance gaps or issues in your foundational infrastructure, reducing the risk of non-compliance for the applications built upon it. Use the following high-level technical approach for this phase of assessment.
- Build your AWS landing zone with HITRUST controls. See Building a landing zone for more information.
- Use AWS and configure services according to the HITRUST requirements that are applicable to your infrastructure scope.
- The HITRUST on AWS Quick Start guide is a reference for building HITRUST with one account. You can use the guide as a starting point to build a multi account architecture.
HITRUST Phase 2 – HITRUST application assessment phase:
During this phase, you examine your AWS workload application accounts to conduct HITRUST assessments for application systems that are running within the AWS landing zone. You have the option to inherit environment-related controls that have been certified as HITRUST compliant within the landing zone in the previous phase.
The following key steps are recommended in this phase:
- Readiness assessment for application scope: Conduct a thorough readiness assessment focused on the application scope, and define boundaries with scoped applications (AWS workload accounts).
- HITRUST application controls: Gather specific HITRUST requirements for application scope by creating a HITRUST object for the application scope.
- Scoped requirements analysis: Analyze requirements and use requirements that can be inherited from Phase 1 of the infrastructure assessment.
- Gap analysis: Work with subject matter experts to conduct a gap analysis, and develop policies, procedures, and implementations for application specific controls.
- Remediation: Remediate the gaps identified during the gap analysis activity.
- Formal r2 assessment: Work with a third-party assessor to initiate a formal r2 validated assessment with HITRUST.
Conclusion
By breaking the compliance process into distinct phases, you can concentrate your resources on specific areas and prioritize essential assets accordingly. This approach supports a focused strategy, systematically addressing critical controls, and helping you to fulfill compliance requirements in a scalable manner. Obtaining the initial certification for the infrastructure and platform layers establishes a robust foundational architecture for subsequent phases, which involve application systems.
Earning certification at each phase provides tangible evidence of progress in your compliance journey. This achievement instills confidence in both internal and external stakeholders, affirming your organization’s commitment to security and compliance.
For guidance on achieving, maintaining, and automating compliance in the cloud, reach out to AWS Security Assurance Services (AWS SAS) or your account team. AWS SAS is a PCI QSAC and HITRUST External Assessor that can help by tying together applicable audit standards to AWS service-specific features and functionality. They can help you build on frameworks such as PCI DSS, HITRUST CSF, NIST, SOC 2, HIPAA, ISO 27001, GDPR, and CCPA.
If you have feedback about this post, submit comments in the Comments section below. If you have questions about this post, start a new thread on the AWS Security, Identity, & Compliance re:Post or contact AWS Support.
Want more AWS Security news? Follow us on Twitter.
Author: Abdul Javid
