
Adding threat detection to custom authentication flow with Amazon Cognito advanced security features
Recently, passwordless authentication has gained popularity compared to traditional password-based authentication methods… You can use Amazon Cognito to customize user authentication flow by implementing passwordless authentication… Additionally, Amazon Cognito provides secure authentication flo…
Recently, passwordless authentication has gained popularity compared to traditional password-based authentication methods. Application owners can add user management to their applications while offloading most of the security heavy-lifting to Amazon Cognito. You can use Amazon Cognito to customize user authentication flow by implementing passwordless authentication. Amazon Cognito enhances the security posture of your applications because it handles the storage and management of user information securely. Additionally, Amazon Cognito provides secure authentication flow and verifiable tokens.
This post explores how you can use the advanced security features of Amazon Cognito to add threat detection to your passwordless authentication custom authentication flow, further strengthening your defenses against account takeover risks.
Overview
Amazon Cognito is a customer identity and access management (CIAM) service that streamlines the process of building secure, scalable, and user-friendly authentication solutions. With Amazon Cognito, you can integrate user sign-up, sign-in, and access control functionalities into your web and mobile applications. One of the key features of Amazon Cognito is that it supports custom authentication flow, which you can use to implement passwordless authentication for your users or you can require users to solve a CAPTCHA or answer a security question before being allowed to authenticate.
Custom authentication flows, such as passwordless authentication, offer an improved user experience while enhancing security by using strong custom factors. In addition, it is recommended to implement additional measures to detect and mitigate potential risks. Amazon Cognito advanced security provides a suite of powerful features designed to detect risks and allows you to take action to protect your user accounts.
For more information on the features offered by Amazon Cognito advanced security, see User pool advanced security features.
By combining passwordless authentication with Amazon Cognito advanced security features, you can enhance your application’s overall security posture while providing a seamless and user-friendly authentication experience to your users.
Advanced security support for custom authentication flow
Amazon Cognito advanced security now supports custom authentication flows to provide additional threat detection, including passwordless authentication. You can improve the security of applications that use custom authentication factors by enabling risk detection and adaptive authentication.
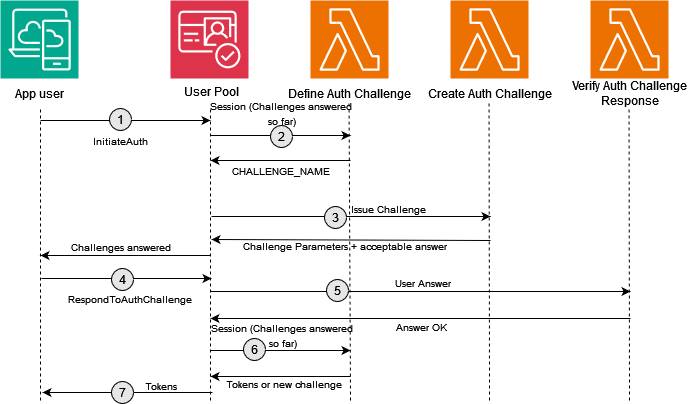
The custom authentication flow triggers three AWS Lambda functions, as shown in Figure 1.

Figure 1: Custom authentication flow
The custom authentication flow depicted in Figure 1 includes the following steps:
- A user initiates authentication from the custom sign-in page, which sends the authentication request to the Amazon Cognito user pool.
- The user pool calls the
Define Auth ChallengeLambda function. This function determines which custom challenge needs to be created. At the end, it reports back to Amazon Cognito to issue a token if authentication is successful. The function is invoked at the start of the custom authentication flow and after each completion of theVerify Auth Challenge ResponseLambda trigger. - The user pool calls the
Create Auth ChallengeLambda function. This function is invoked to create a unique challenge for the user based on the instruction of theDefine Auth ChallengeLambda trigger. - The user responds to the challenge with their answer, which is sent by making a
RespondToAuthChallengeAPI call to the Amazon Cognito user pool. - The user pool calls the
Verify Auth ChallengeResponse Lambda function with the response from the user. The function determines if the answer is correct. - The user pool then calls the
Define Auth ChallengeLambda function. This function verifies that the challenge has been successfully answered and that no further challenge is needed. It includesissueTokens: truein its response to the user pool. - When advanced security is enabled, Amazon Cognito performs risk analysis on the authentication request. If a risk is detected, it’s mitigated as configured in advanced security. The user pool now considers the user to be authenticated and sends the user a valid JSON Web Token (JWT) (in response to step 4, the authentication challenge).
How to configure advanced security for custom authentication flow
In this section, you set up a custom passwordless authentication flow and then add advanced security features (ASF) to protect your existing authentication flow.
Configure advanced security features
- Start by implementing passwordless authentication with Amazon Cognito and WebAuthn.
- After setting up passwordless authentication, go to the AWS Management Console for Amazon Cognito and configure advanced security features for your passwordless authentication flow.
- Navigate to the user pool that has been created for the passwordless authentication solution.
- Choose the Advanced Security tab and choose Activate.
- In the Included features and initial states pop-up, you’ll see the Threat protection for standard authentication and Threat protection for custom authentication have already been included in Audit-only mode, choose Activate.
Note: It’s recommended to run advanced security features in audit only mode initially to evaluate risk patterns and decide the appropriate settings for each risk level.

Figure 2: Activate advanced security features
- To set up full function mode and enforcement for Threat protection for custom authentication, choose Set up full-function mode.

Figure 3: Activate threat protection for custom authentication flow
- For Custom authentication enforcement mode, you can select:
- No enforcement – Amazon Cognito doesn’t gather metrics on detected risks or automatically take preventive actions.
- Audit-only – Amazon Cognito gathers metrics on detected risks, but doesn’t take automatic action.
- Full-function – Amazon Cognito automatically takes preventive actions in response to different levels of risk that you configure for your user pool.
Select Full-function.

Figure 4: Configure enforcement level
- You can choose either Cognito defaults or Custom to respond to each level of risk when Amazon Cognito detects potential malicious activity.
- Cognito defaults will block sign-in attempts for low, medium, and high risks.

Figure 5: Adaptive authentication configuration
- If you choose Custom, you can customize the risk configuration for each risk level.
- Allow – Sign-in attempts will be allowed without additional authentication factors.
- Optional MFA – Amazon Cognito will send a multi-factor authentication (MFA) challenge to the user if the user is eligible for MFA. A user is eligible for MFA if:
- They have configured an authenticator app and TOTP MFA is enabled for the user pool.
- They have a phone number or email address, and SMS or email message MFA is enabled for the user pool.
If the user is eligible for MFA, they must respond correctly to the MFA challenge. If the user is not eligible for MFA, Cognito will allow sign-in without additional authentication factors.
- Require MFA – Amazon Cognito will send an MFA challenge to the user if the user is eligible for MFA. If the user is eligible for MFA, they must respond correctly to the MFA challenge. If the user is not eligible for MFA, Cognito will block the sign-in attempt.
- Block – Cognito blocks future sign-in attempts.
- Cognito defaults will block sign-in attempts for low, medium, and high risks.
- You can notify users when adaptive authentication detects potentially suspicious activity using a customized email message. This notification is sent to users to confirm their activity, and Amazon Cognito uses the user’s response to learn their behavior patterns over time. By customizing the notification message, you can provide a better user experience and make sure communication regarding the security measure is clear to your users.

Figure 6: Adaptive authentication message template
- Review the threat protection configuration.

Figure 7: Custom auth flow threat protection configuration
Test the configuration
To test the configuration, sign in from multiple devices and locations. Amazon Cognito will calculate risk and take action based on your configuration. After you’ve signed in multiple times through different devices, you can view the User event history.
- In the Amazon Cognito console, go to the user pool and search for the user you signed in as.
- Select the user name and navigate to User event history.

Figure 8: User event history
You can see the user event history with the risk levels and actions taken by Amazon Cognito as shown in Figure 8. In the figure, Amazon Cognito advanced security has detected a high-risk event and has blocked the sign-in attempt.
Amazon Cognito will associate a risk level with each sign-in attempt and based on your adaptive configuration; it will either allow the sign in, request an MFA response, or block the request.
Note: Populating
UserContextDatain the request is important to the functionality of the risk engine. Some SDKs, such as AWS Amplify, will populate this object by default, but in custom code, you need to make sureuserContextDatais calculated and populated correctly in relevant events. See Adding user device and session data to API requests for more information about populatinguserContextData.
Additionally, you can export user authentication event history to Amazon CloudWatch, a Amazon Data Firehose stream, or an Amazon Simple Storage Service (Amazon S3) bucket for further analysis of the security event.
Conclusion
In this post, you learned how to enable threat detection for a custom authentication flow such as passwordless authentication in Amazon Cognito. Threat detection helps you to monitor user activity and enhances security measures even when your users sign in through a custom authentication flow.
If you have feedback about this post, submit comments in the Comments section below.
Author: Vishal Jakharia






