
How to create an AMI hardening pipeline and automate updates to your ECS instance fleet
Amazon Elastic Container Service (Amazon ECS) is a comprehensive managed container orchestrator that simplifies the deployment, maintenance, and scalability of container-based applications… With Amazon ECS, you can deploy your containerized application as a standalone task, or run a task as part o…
Amazon Elastic Container Service (Amazon ECS) is a comprehensive managed container orchestrator that simplifies the deployment, maintenance, and scalability of container-based applications. With Amazon ECS, you can deploy your containerized application as a standalone task, or run a task as part of a service in your cluster. The Amazon ECS infrastructure for tasks includes Amazon Elastic Compute Cloud (Amazon EC2) instances in the AWS Cloud, serverless (AWS Fargate) in the AWS Cloud, or on-premises virtual machines (VMs) or servers. You can enable auto-scaling for Amazon ECS capacity providers when using EC2 instances, allowing your infrastructure to dynamically adjust based on workload demands. You define the infrastructure type or the capacity providers where you deploy your tasks or services.
You can choose EC2 instances as the computing resources for your ECS cluster, which allows you to control your cluster’s underlying infrastructure, including the size of EC2 instances, the instance operating system, and extra security controls required by a compliance framework. AWS recommends that you use Amazon ECS-optimized Amazon Machine Images (AMIs), which are set up with the requirements and recommendations to efficiently run your container workloads on Amazon Linux instances. We recommend that you refresh your container instances fleet with the latest ECS-optimized AMIs to include the latest bug fixes and feature updates. However, managing and updating your container instance fleet might become complex as your Amazon ECS workload grows.
In this blog post, I will show you how to create a workflow to enhance Amazon ECS-optimized AMIs by using the CIS Docker Benchmark and automatically updating your EC2 instances in your ECS cluster with the newly created AMIs.
Overview of CIS Docker Benchmark
The CIS Docker Benchmark provides prescriptive guidance for establishing a secure configuration posture for a Docker container engine, container host, container images and build files. The CIS Docker Benchmark has seven sections about Docker and container security:
- Host configuration
- Docker daemon configuration
- Docker daemon configuration files
- Container images and build file configuration
- Container runtime configuration
- Docker security operations
- Docker swarm configuration
The solution described in this post covers sections 1, 2, and 3 of the CIS Docker Benchmark, including security recommendations to prepare the host machine used for Amazon ECS workloads, securing the behavior of the Docker daemon (server), and securing Docker-related files and directory permissions and ownerships. However, the solution doesn’t implement all of the controls listed in these three sections. For a complete list of controls implemented, see the solution’s repository.
Solution overview
EC2 Image Builder is a fully managed AWS service, designed to simplify the process of creating, handling, and implementing server images that are custom, secure, and consistently updated. For this solution, you will deploy an EC2 Image Builder pipeline to apply the CIS Docker Benchmarks to an Amazon ECS-optimized AMI and use the created AMI to refresh the Amazon ECS instance fleet. This solution is customizable, so you can select the security controls to harden your base AMI. You can also specify cluster tags during CloudFormation template deployment; these tags will filter the ECS clusters that you have included in the Amazon EC2 instance refresh process. I’ve provided an AWS CloudFormation template that you can use to provision the necessary resources.

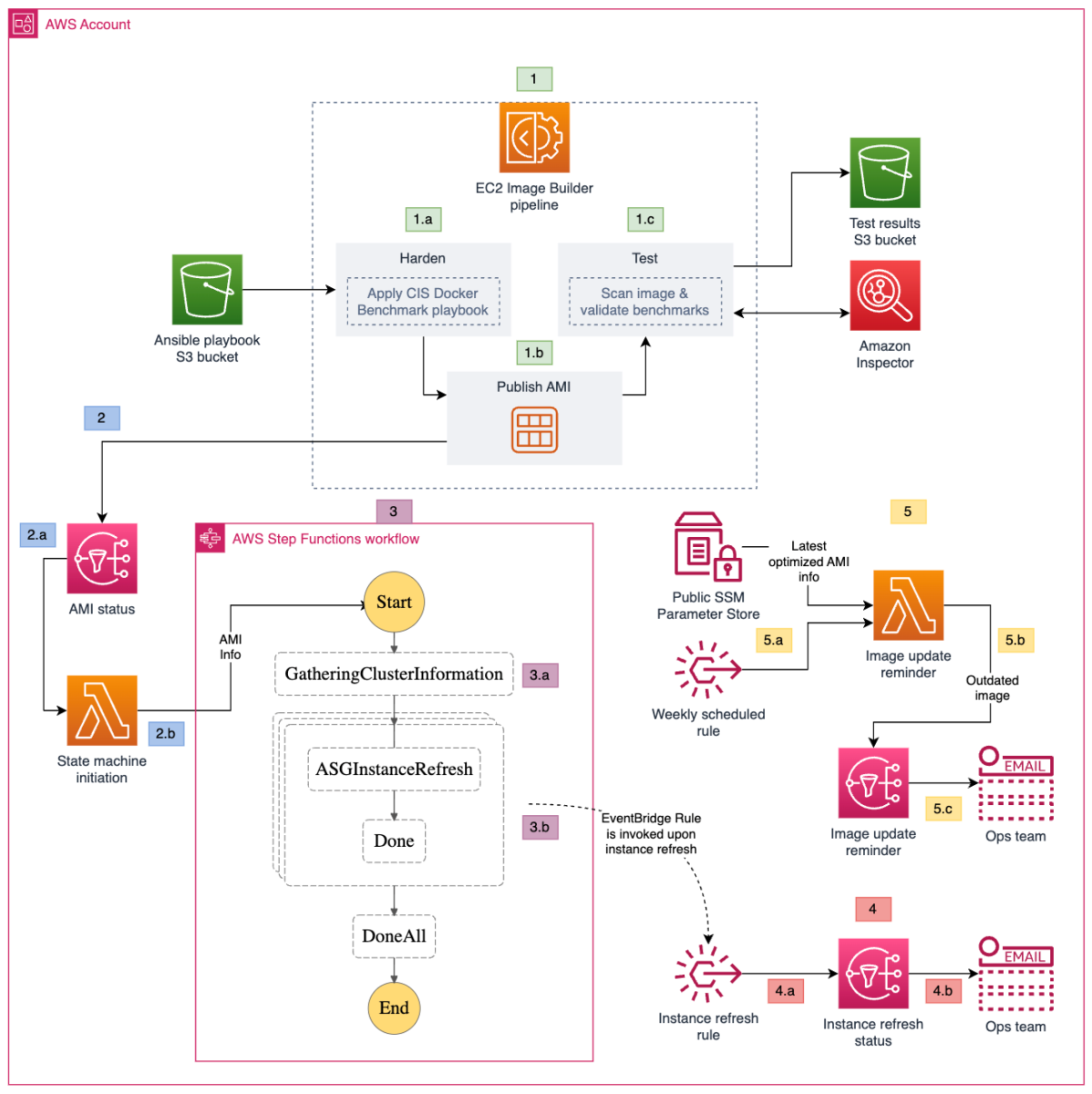
Figure 1: Amazon ECS instance refresh workflow
As shown in Figure 1, the solution involves the following steps:
- EC2 Image Builder
- The AMI image pipeline downloads the ansible playbook from the S3 bucket, and runs it against the base image.
- The pipeline publishes the hardened AMI.
- The pipeline validates the benchmarks applied to the base image and publishes the results to a test results S3 bucket. It also invokes Amazon Inspector to run a vulnerability scan on the published image.
- State machine initiation
- When the AMI is successfully published, the pipeline publishes a message to the AMI status SNS topic. The SNS topic invokes the State machine initiation Lambda function.
- The State machine initiation Lambda function extracts the image ID of the published AMI and uses it as the input to initiate the state machine.
- State machine
- The first state gathers information related to Amazon ECS clusters, including the capacity providers for the EC2 auto scaling group. It creates a new launch template version with the hardened AMI image ID for the EC2 auto scaling group.
- The second state uses the new launch template to initiate an instance refresh for the EC2 auto scaling group.
- Instance refresh status update
- The instance refresh rule selects the auto scaling group instance refresh events (failure, success, and cancellation events) and sends them to the Instance refresh status SNS topic.
- The Instance refresh status SNS topic sends an email on the instance refresh status to subscribers.
- Image update reminder
- A weekly scheduled rule invokes the Image update reminder Lambda function.
- The Image update reminder Lambda function retrieves the value for LatestECSOptimizedAMI from the CloudFormation template, and extracts the last modified date of the Amazon ECS-optimized AMI used as the base image in the EC2 Image Builder pipeline. It compares the last modified date of the AMI with the creation date of the latest AMI published by the pipeline. If a new base image is available, it publishes a message to the image update reminder SNS topic.
- The Image update reminder SNS topic sends a message to subscribers notifying them of a new base image. You need to create a new version of your image recipe to update it with the new AMI.
Prerequisites
To follow along with this walkthrough, make sure that you have the following prerequisites in place:
- An AWS account
- Permission to create required resources
- An existing ECS cluster with one or more EC2 capacity providers
- AWS Command Line Interface (AWS CLI) installed
- Amazon Inspector for EC2 enabled in your AWS account
Walkthrough
To deploy the solution, complete the following steps.
Step 1: Download or clone the repository
The first step is to download or clone the solution’s repository.
To download the repository
- Go to the main page of the repository on GitHub.
- Choose Code, and then choose Download ZIP.
To clone the repository
- Make sure that you have Git installed.
- Run the following command in your terminal:
git clone https://github.com/aws-samples/ecs-image-hardening-and-instance-refresh.git
Step 2: Create an S3 bucket
Amazon Simple Storage Service (Amazon S3) is an object storage service that offers industry-leading scalability, data availability, security, and performance. An S3 bucket is a container for objects stored on Amazon S3. For this walkthrough, you need to create an S3 bucket and copy the content of the ansible folder to your newly created bucket. Make a note of your S3 bucket name because you will need it in the next step.
Step 3: Create the CloudFormation stack
In this step, you deploy the solution’s resources by creating a CloudFormation stack using the provided CloudFormation template. Sign in to your account and choose an AWS Region where you want to create the stack. Make sure that the Region you choose supports the services used by this solution. To create the stack, follow the steps in Creating a stack on the AWS CloudFormation console. Note that you need to provide values for the parameters defined in the template to deploy the stack. The following table lists the parameters that you need to provide.
| Parameter | Description |
| AnsiblePlaybookArguments | ansible-playbook command arguments |
| AnsiblePlaybookBucket | S3 bucket name containing ansible playbook |
| CloudFormationUpdaterEventBridgeRuleState | Amazon EventBridge rule that invokes the Lambda function that checks for a new version of the EC2 Image Builder parent image |
| ClusterTags | Tags in JSON format to filter the ECS clusters that you want to update |
| ComponentName | Name of the EC2 Image Builder component |
| DistributionConfigurationName | Name of the EC2 Image Builder distribution configuration |
| EnableImageScanning | Choose whether or not to enable Amazon Inspector image scanning |
| ImagePipelineName | Name of the EC2 Image Builder pipeline |
| InfrastructureConfigurationName | Name of the EC2 Image Builder infrastructure configuration |
| InstanceType | EC2 Image Builder infrastructure configuration EC2 instance type |
| LatestECSOptimizedAMI | ECS-optimized AMI parameter name; for more info, see Retrieving Amazon ECS-optimized AMI metadata |
| libDockerVolumeSize | Container partition size in gigabytes (GB) |
| libDockerVolumeType | Container partition volume type |
| RecipeName | Name of the EC2 Image Builder recipe |
| RootVolumeSize | AMI root partition volume size in GB |
| RootVolumeType | AMI root partition volume type |
Step 4: Set up Amazon SNS topic subscribers
Amazon Simple Notification Service (Amazon SNS) is a web service that coordinates and manages the delivery or sending of messages to subscribing endpoints or clients. An Amazon SNS topic is a logical access point that acts as a communication channel.
The solution in this post creates three Amazon SNS topics to keep you informed of each step of the process. The following is a list of the topics that the solution creates and their purpose.
- AMI status topic – a message is published to this topic upon successful creation of an AMI.
- Image update reminder topic – a message is published to this topic if a newer version of the base Amazon ECS-optimized AMI is published by AWS.
- Instance refresh status topic – a message is published to this topic each time that an ECS cluster capacity provider gets an instance fleet refresh.
You need to manually modify the subscriptions for each topic to receive messages published to that topic.
To modify the subscriptions for the topics created by the CloudFormation template
- Sign in to the Amazon SNS console.
- In the left navigation pane, choose Subscriptions.
- On the Subscriptions page, choose Create subscription.
- On the Create subscription page, in the Details section, do the following:
- For Topic ARN, choose the Amazon Resource Name (ARN) of one of the topics that the CloudFormation topic created.
- For Protocol, choose Email.
- For Endpoint, enter the endpoint value. In our example, this is an email address, such as the email address of a distribution list.
- Choose Create subscription.
- Repeat the preceding steps for the other two topics.
Step 5: Run the pipeline
The EC2 Image Builder pipeline that the solution creates consists of an image recipe with one component, an infrastructure configuration, and a distribution configuration. I’ve set up the image recipe to create an AMI, select a base image, choose components, and define block device mapping. There’s only one component where building and testing steps are defined. For the building step, the solution creates a separate partition for /var/lib/docker and mounts it to a dedicated device specified in the image recipe. It then applies the CIS Docker Benchmark ansible playbook and cleans up the unnecessary files and folders. In the test step, the solution runs Amazon inspector, a continuous assessment service that scans your AWS workloads for software vulnerabilities and unintended network exposure, and Docker Bench for Security. Optionally, you can create your own components and associate them with the image recipe to make further modifications on the base image.
You will need to manually run the pipeline by using either the AWS Management Console or AWC CLI.
To run the pipeline (console)
- Open the EC2 Image Builder console.
- From the pipeline details page, choose the name of your pipeline.
- From the Actions menu at the top of the page, select Run pipeline.
To run the pipeline (AWS CLI)
- Make sure that you have properly configured your AWS CLI.
- Run the following command. Replace <pipeline region> with your own information.
aws imagebuilder list-image-pipelines –region <pipeline region>
- From the list of pipelines, find the pipeline named ECSAnsiblePipeline and note the pipeline ARN, which you will use in the next step.
- Run the pipeline. Make sure to replace <pipeline arn> and <region> with your own information.
aws imagebuilder start-image-pipeline-execution –image-pipeline-arn <pipeline arn> –region <region>
The following is a process overview of the image hardening and instance refresh:
- Image hardening – when you start the pipeline, EC2 Image Builder creates the required infrastructure to build your AMI, applies the ansible playbook (CIS Docker Benchmark) to the base AMI, and publishes the hardened AMI. A message is published to the AMI status topic as well.
- Image testing – after publishing the AMI, EC2 Image Builder scans the newly created AMI with Amazon Inspector and reports the findings back. It also runs Docker Bench for Security to verify the changes that the ansible playbook made to the base AMI and publishes the results to an S3 bucket.
- State machine initiation – after a new AMI is successfully published, the AMI status topic invokes the State machine initiation Lambda function. The Lambda function invokes the instance refresh state machine and passes on the AMI info.
- Instance refresh – the instance refresh state machine has two steps:
- Gather cluster information – a Lambda function gathers information regarding EC2 capacity providers and their associated auto scaling groups. For each auto scaling group, it creates a new launch template and includes the hardened AMI information. When you create the CloudFormation stack, if you pass a tag or a list of tags, only clusters with matching tags are processed in this step.
- Auto scaling group instance refresh – the state machine uses the output of the first Lambda function (first state) and starts instance refresh for auto scaling groups in parallel (second state). An EventBridge rule publishes a message to the Instance refresh status topic upon successful refresh of each auto scaling group.
This solution also creates an EventBridge rule that is invoked weekly. This rule invokes the Image update reminder Lambda function, and notifies you if a new version of your base AMI has been published by AWS so that you can run the pipeline and update your hardened AMI.
Conclusion
In this blog post, you learned how to create a workflow to harden Amazon ECS-optimized AMIs by using the CIS Docker Benchmark and to automate the refresh of EC2 instances in your ECS clusters. This automated workflow has several advantages. First, it helps ensure a consistent and standardized process for image hardening, reducing potential human errors and inconsistencies. By automating the entire process, you can apply security and compliance standards across your instances. Second, the tight integration with AWS Step Functions enables smooth, orchestrated updates to the ECS cluster instances, enhancing the reliability and predictability of deployments. This automation also reduces manual intervention, helping you achieve time savings so that your teams can focus on more value-driven tasks. Moreover, this systematic approach helps to enhance the security posture of your Amazon ECS workloads because you can address vulnerabilities rapidly and systematically, helping to keep the environment resilient against potential threats.
If you have feedback about this post, submit comments in the Comments section below. If you have questions about this post, contact AWS Support.
Want more AWS Security news? Follow us on Twitter.
Author: Nima Fotouhi
