
How to support OpenID AuthZEN requests with Amazon Verified Permissions
RestApiEndpoint1234567A = https://abcdef0123…authSecret’) Install the dependencies and perform the test by running the following command: $ yarn$ yarn build$ yarn test https://abcdef0123…com/prod/ console The following interoperability results display in the console: …
OpenID Foundation’s AuthZEN Working Group is currently drafting a new specification (version 1.0, draft 03 at the time of publication) and associated standard mechanisms, protocols, and formats to communicate authorization-related information between components involved in access control and authorization.
Today, we’re publishing an open-source reference implementation demonstrating seamless integration between an AuthZEN-compliant policy enforcement point (PEP) and Amazon Verified Permissions, a fully managed AWS service for storing authorization policies (expressed in Cedar policy language) and evaluating authorization requests at runtime.
What is OpenID AuthZEN specification?
Traditionally, application developers built their own authorization logic within the application code to evaluate access to resources. Reviewing the authorization rules requires reviewing the application code, and changing the authorization rules requires changing and deploying a new version of the application. Customers using this pattern often find it challenging to consistently enforce their authorization rules, track changes to these rules, and update rules as their application evolves.
To solve these challenges, modern application designs have shifted their authorization capabilities and decoupled them from application code. This strategy accelerates application development and grants fine-grained permissions within applications in a more repeatable and dynamic way that developers can apply consistently. Fine-grained permissions are typically designed based on:
- Subject role assignments following role-based access control (RBAC)
- Attribute values of the subject or the requested resources following attribute-based access control (ABAC)
- Relationships between subjects and resources following relationship-based access control (ReBAC)
- A hybrid model using a combination of the preceding methods
Expressions of these access control rules are called policies, which lead to the policy-based access control (PBAC) approach.
To support these access control approaches, customers implement solutions that follow the guidance of NIST SP 800-162 – A guide to ABAC.

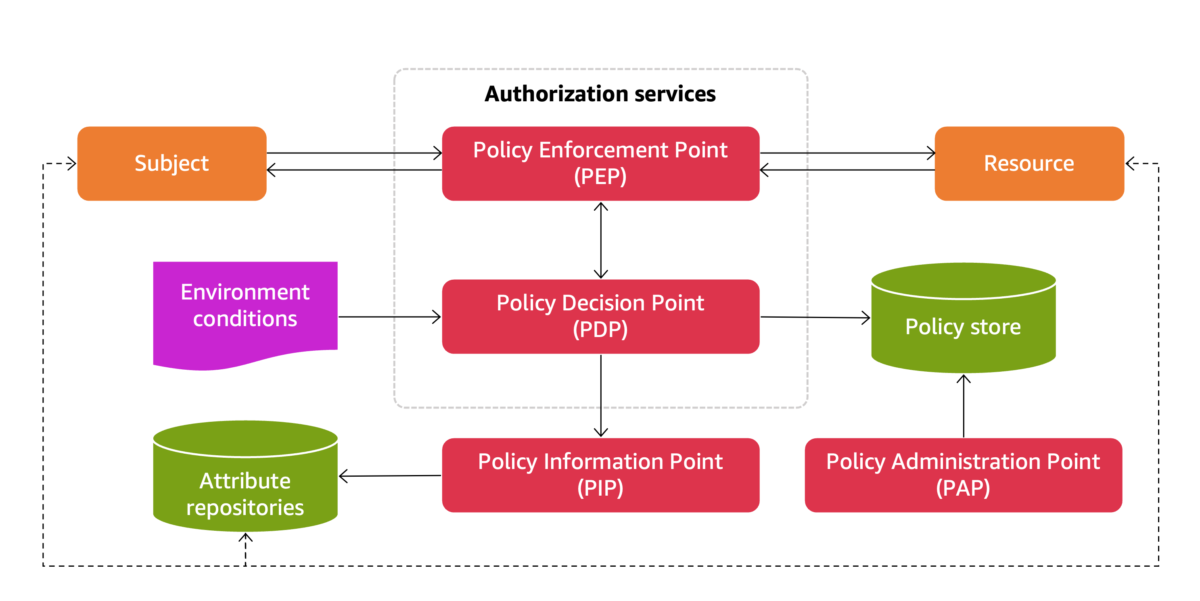
Figure 1: Access control components and interactions
Figure 1 illustrates the architecture of an advanced access control mechanism that consists of several key components that work together to manage and enforce authorization policies.
At the heart of this system is the policy decision point (PDP), which serves as the rules or policy engine. The PDP is responsible for evaluating rules and policies to determine whether a particular access request should be allowed or denied. This component interacts closely with the policy enforcement point (PEP), which acts as the gatekeeper for resource access.
The PEP, typically integrated into your application, receives access requests for subjects (users or systems) and enforces the decisions made by the PDP. It either allows or denies access to the requested resource based on the PDP’s determination.
To make informed decisions, the PDP might need to retrieve additional metadata or attributes. A policy information point (PIP) acts as an interface to external data sources, such as subject attribute and resource attribute stores. These could include databases such as your HR system, providing crucial contextual information to aid in the decision-making process.
The diagram also shows other important elements:
- The policy store, which stores the authorization policies.
- The policy administration point (PAP), used for managing and updating policies in the policy store.
- Environment conditions, which can influence access decisions based on factors like time, location, or system status.
All these components collaborate within the authorization services framework to provide a comprehensive and flexible access control system. The AuthZEN specification provides a standardized way to communicate authorization requests from the PEP to the PDP and to communicate authorization decisions from the PDP to the PEP.
Interoperability with Verified Permissions
Verified Permissions offers organizations a fully managed service that combines the roles of both a PDP engine and a policy store with a PAP. AWS manages the underlying infrastructure, scaling automatically with application demands and maintaining consistent performance across distributed systems.
Verified Permissions uses Cedar, an open-source policy language that brings mathematically provable access control. When integrated into an application’s architecture, Verified Permissions serves as the central decision-making engine for authorization requests sent through its IsAuthorized() API. Verified Permissions evaluates requests against defined policies while considering information such as principal attributes, resource properties, type of action, and environmental conditions. The service also offers the ability to group common authorization requests into one API call and to validate OAuth 2.0 JSON Web Token with the OpenID Connect provider that issued it when provided as principal information.
This reference implementation enables interoperability and seamless integration between OpenID’s AuthZEN protocol and Verified Permissions. It can help you standardize authorization patterns across different services hosted on AWS.
Architecture overview
The architecture of the proposed AuthZEN interface for Verified Permissions is illustrated in Figure 2.

Figure 2: Architecture overview
The workflow for this architecture is as follows:
- The application, serving as PEP, makes an authenticated authorization API call for access requests in AuthZEN-compliant format.
- Amazon API Gateway invokes an AWS Lambda authorizer to evaluate the PEP authentication mechanism of the choice.
Note: In this solution, you will manage access to the API using a secret generated by AWS Secrets Manager. Review your threat model and adopt additional authentication mechanisms that fit your workload such as OAuth 2.0 bearer tokens, client certificate authentication, or AWS Identity and Access Management (IAM) temporary credentials.
- After successful authentication, API Gateway propagates the request to a Lambda function integration.
- The Lambda function queries the entity store, which is a PIP, to retrieve additional metadata and attributes about the entities in the authorization request. The entities are representing the principals and the resources.
- The Lambda function integration transforms the authorization requests in AuthZEN format into a Verified Permissions
IsAuthorized()formatted request. - Verified Permissions evaluates the authorization request and returns the authorization decision, then a Lambda function transforms the authorization decision to an AuthZEN formatted decision back to the application.
Deploy the solution
You can deploy the authzen-interface-verified-permissions solution by using the AWS Cloud Development Kit (AWS CDK). Solution artifacts are available in the aws-samples/sample-authzen-interface-verified-permissions repository.
For instructions and more information on using the AWS CDK, see Get started with the AWS CDK.
Deploy the policy store
Create a Verified Permissions policy store to store your authorization policies. You can create a new policy store using the AWS Management Console for Verified Permissions or deploy the sample policy store by using AWS CDK. The sample policy store contains Cedar policies and entities to support AuthZEN’s authorization scenarios.
To deploy the policy store stack using AWS CDK:
- Navigate to the project root folder, bootstrap your environment, and deploy the policy store by using the following commands. Replace
<account-id>and<region>with your AWS account number and the AWS Region you want to deploy in. - After the deployment completes, locate the
PolicyStoreIdandCedarEntitiesTableNamefrom Outputs: - Set the policy store ID and entities table name as environment variables:
Deploy AuthZEN interface for Verified Permissions
You then deploy a sample AuthZEN PDP interface that’s connected to the Verified Permissions policy store. The PDP includes the API Gateway REST API, the Lambda authorizer, and the Lambda function integration.
To deploy the PDP by using AWS CDK:
- Deploy the PDP stack by using the following commands:
If you have a custom domain for the API Gateway endpoint, visit the CDK stack for AuthZEN HTTPS binding section for more information.
- After the deployment, locate the API endpoint and secret from Outputs. This is your AuthZEN authorization endpoint.
Test the deployment
The OpenID AuthZEN working group has defined a set of interoperability scenarios based on a sample Todo application as the PEP. You can view the payload specification for each API authorization request and test it with AuthZEN’s API Gateway test runner.
To test the deployment:
- Clone AuthZEN API Gateway test runner and navigate to the
test-harnessdirectory. - Set the secret ARN in the environment variable.
- Set the predefined AuthZEN test runner’s environment variable for the Authorization header value.
- Install the dependencies and perform the test by running the following command:
- The following interoperability results display in the console:
The PASS REQ results indicate this deployment has met AuthZEN interoperability test scenarios requirements. You can also view the latest results at OpenID AuthZEN Interop results summary site.
It’s your turn to build
In this post, we introduced an open-source AuthZEN interface for Amazon Verified Permissions that’s based on the OpenID Foundation’s AuthZEN working group specifications. This implementation provides developers with a transparent way to adopt industry-standard authorization practices while maintaining the security and scalability benefits of the managed authorization service provided by AWS.
If you’re interested in learning more about Cedar and Verified Permissions, see the following references:
- How we designed Cedar to be intuitive to use, fast, and safe
- Authorize API Gateway APIs using Amazon Verified Permissions with Amazon Cognito or bring your own identity provider
- Cedar permissions model design patterns
If you’re interested in this new specification, join the AuthZEN Working Group and provide your feedback through the associated GitHub repository.
If you have feedback about this post, submit comments in the Comments section below.
Author: Edward Sun
