
Inside the federated authentication system of Amazon Game Studios
To address these challenges, Amazon Game Studios used Amazon Web Services (AWS) to create a solution that would allow integration with a single, unified authentication API, while seamlessly supporting various gaming platforms behind the scenes… We will show how Amazon Game Studios implemented a …
In the complex ecosystem of gaming, players expect seamless experiences across multiple platforms, such as PlayStation, Xbox, Steam, and mobile app stores. Each platform maintains its own authentication protocols, token formats, and security requirements. This creates a fragmented landscape that poses significant challenges for game developers and infrastructure teams. To address these challenges, Amazon Game Studios used Amazon Web Services (AWS) to create a solution that would allow integration with a single, unified authentication API, while seamlessly supporting various gaming platforms behind the scenes.
We will show how Amazon Game Studios implemented a unified authentication system that abstracts the complexities of various platform identities into a single JSON Web Token (JWT). The solution resulted in more efficient client authentication for games, successfully supporting over a million concurrent players. It also improved the efficiency of the security and privacy review processes of Amazon Game Studios.
Note: User identity and data management involve privacy and regulatory considerations (especially for players under 18 years of age). Those considerations are outside the scope of this discussion.
Challenges Amazon Game Studios was facing
Before implementing the unified solution, Amazon Game Studios struggled with a fragmented authentication landscape that created significant bottlenecks for developers. Each gaming platform required game developers to implement separate authentication workflows with distinct APIs, token formats, and security protocols.
This level of complexity forced development teams to spend considerable time integrating multiple authentication systems for each new game release. This resulted in a slower time-to-market (approximately 1-2 additional weeks) and increased development costs.
Additionally, the lack of a centralized identity management system made it difficult for the Amazon Game Studios developers to conduct comprehensive security and regulatory reviews. They had to evaluate each platform integration individually. Having a decentralized approach meant security audits would involve examining multiple different authentication endpoints, each having their own unique vulnerability profiles and compliance requirements.
Solution requirements
In designing a solution for this use case, Amazon Game Studios had several requirements for authentication, authorization, and token expiration:
- Authentication:
- Ability to validate the platform token with the platform providers.
- Ability to verify that a player is valid and has game access.
- Ability to validate the Amazon Game Studios ID (identity) tokens if present—These are tokens that are created when a player creates an account from within Amazon Game Studios or websites.
- Ability to return platform account information, Amazon Game Studios account information, and persona IDs (game-specific obfuscated player IDs).
- Authorization:
- Integration with the moderation service that verifies player penalties.
- Ability to restrict a player’s access to obtain tokens if they have been banned from the game.
- Ability to block players by geolocation.
- Token expiration:
- Ability to successfully handle scenarios that can invalidate the state of a token.
Key decisions
Handling different authentication requirements
Gaming platforms such as Xbox, Steam, PlayStation, Nintendo, and Luna each implement unique authentication systems that contain different token structures, validation requirements, and security protocols. This created a high level of complexity for Amazon Game Studios, who needed to integrate with these platforms while maintaining consistent security standards.
Amazon Game Studios addressed the issue of handling various platform-specific tokens by creating a Federated Token Service (FTS) that converts tokens into a standardized JWT format. This format contains a consistent set of claims that all game services can leverage in a uniform way. When a game passes a platform authentication token to the FTS, the FTS decrypts the token and validates its integrity. It also creates another token, which contains standardized claims, that provides game services with a way to access games in a consistent way, regardless of the platform that a player is using.
The standardized JWTs that are generated by the FTS serve two primary use cases within the Amazon Game Studios architecture. First, when calling other game services directly, games can pass the JWT to those services, which can then validate the JWT. It can extract player identity information without needing to understand platform-specific authentication formats.
Second, for integrations with solutions that only support server-to-server calls, games can implement a lightweight proxy layer that handles authentication. The proxy layer would handle authentication by using the JWT before making calls to backend services through IAM roles or other server-appropriate methods. For example, when a game needs to make API calls to Amazon Bedrock for generative AI actions, the game client cannot call Amazon Bedrock directly. Instead, the proxy service validates the player’s identity by using the JWT and then delegates the API call to Amazon Bedrock on behalf of the authenticated player.
One of the approaches that the FTS uses to perform validation is making direct API calls to each platform token’s validation endpoints. This provides near real-time verification that the token is legitimate, active, and has not been revoked. Additionally, the solution implements automated key rotation mechanisms that periodically fetch updated public keys from platform key distribution endpoints.
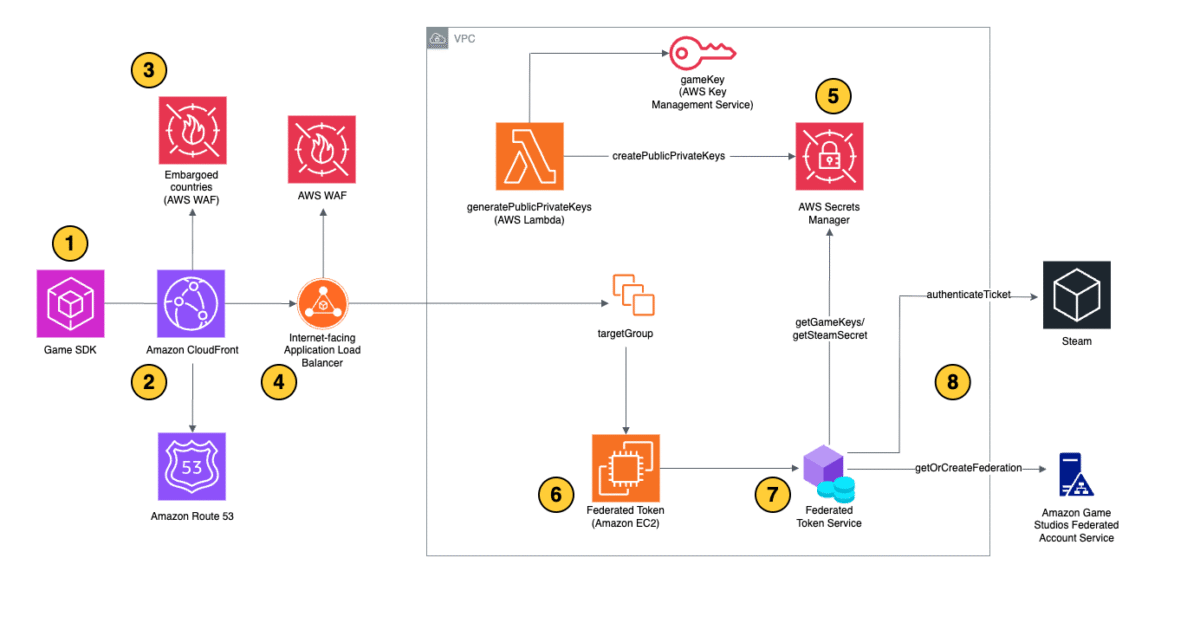
The architecture diagram in Figure 1 illustrates how the Federated Token Service of Amazon Game Studios processes player identifies across multiple gaming platforms. The following items break down each component, and step, in the workflow. It explains how platform-specific authentication tokens are transformed into a standardized format that can be used consistently across Amazon Game Studios:
- Player authentication: A player authenticates with their gaming platform (Luna, Nintendo, PlayStation, Steam, or Xbox) and receives a platform-specific authentication token.
- Token submission: The game client sends the platform-specific authentication token to Amazon CloudFront, which serves as the entry point and content delivery network for the authentication service.
- Security filtering: AWS WAF (integrated with CloudFront) applies security rules to filter the incoming request, including geographic restrictions for embargoed countries and protection against web application attacks.
- Load balancing: The Application Load Balancer (ALB) receives the request from CloudFront and routes it to the appropriate backend services, with AWS WAF also protecting the ALB.
- Secret validation: AWS Secrets Manager provides the rotating secret header that AWS WAF validates to confirm that the request came through the proper CloudFront distribution and not directly to the origin.
- Platform token validation: The FTS running on Amazon Elastic Compute Cloud (Amazon EC2) instances (managed by auto-scaling groups) validates the incoming platform token by making direct API calls to the respective platform’s token validation endpoints.
- Token processing: The Amazon EC2 instances decrypt the platform token—extracting the relevant authentication information and claims from it.
- Security and authorization checks: The FTS performs additional validation checks including:
- Verifying that the player has valid game access
- Checking with the moderation service for any player penalties or bans
- Confirming geographic access permissions
Following these steps, the FTS creates a new standardized JWT that contains consistent claims and player information, regardless of the original platform. The standardized JWT, along with platform account information, Amazon Game Studios account information, and persona IDs, is returned to the game client.
Multiple layers of infrastructure security
To distribute this solution, Amazon Game Studios uses Amazon CloudFront, due to the need for high availability. The CloudFront distribution is integrated with AWS WAF to protect against web application attacks, as well as AWS Shield for distributed denial-of-service (DDoS) prevention. AWS WAF is connected to CloudFront and contains rules that have been configured to enforce geographic restrictions based on game licensing requirements. The system can automatically block traffic from embargoed countries, verifying that players from these countries cannot access the service.
To facilitate automatic secret rotation in AWS Secrets Manager, Amazon Game Studios implemented a solution that connects CloudFront to a public Application Load Balancer (ALB), which is protected by AWS WAF. A secret in Secrets Manager is automatically rotated every seven days, following security best practices for credential management. AWS WAF includes a rule that validates the presence and correctness of the secret header. Any request that lacks this authentication header is automatically denied. This prevents direct access to the origin infrastructure and confirms that all traffic flows through the intended CloudFront distribution.
Designing for scalability and reliability
When designing the unified authentication system, Amazon Game Studios prioritized two key architectural principles:
- Scalability to handle increasing and fluctuating concurrent user loads
- Reliability to verify consistent availability during critical gaming events
For scalability, Amazon Game Studios opted to use ALBs because of their pre-warming capabilities, which can be beneficial for game launches. Load balancers are already scaled to handle anticipated traffic volumes. Additionally, ALBs offer the benefit of adding listener rules that streamline the process of determining how to route requests to registered targets.
To handle increased traffic for game launches and special events, the solution can quickly scale due to its use of Amazon EC2 auto-scaling groups. Amazon Game Studios also implemented configurable token expiration to manage the API load during peak periods.
To support reliability, Amazon Game Studios implemented a fallback system that allows the conditional use of expired tokens during authenticator platform outages. For example, if one of the authenticator platforms happens to be down, the game can pass a refresh token. This is a credential artifact that lets a client application acquire new access tokens without needing to ask the user to log in again. An API will then generate the correct token by using the information that has been embedded into the refresh token.
Overall architecture
Figure 2 illustrates the complete authentication flow within the unified system of Amazon Game Studios. The process begins when a game client initiates authentication by creating or refreshing a token through the Amazon Game Studios Federated Token Service. This service acts as the central hub, communicating with external systems and Amazon API Gateway to retrieve OpenID configuration details and security keys that are needed for token validation.
Once received, the Federated Token Service decrypts the platform-specific authentication token and routes it to the appropriate identity service. Simultaneously, the Federated Token Service works with the Amazon Game Studios Federated Account Service to perform a GetOrCreateFederationAccount operation. This verifies that player accounts are properly linked across platforms.
The Federated Account Service then coordinates with the Amazon Game Studios Identity Service to create shadow accounts and persist federation data across two Amazon DynamoDB databases: one for persona mapping and another for account federation mapping.
This architecture provides Amazon Game Studios with a way to handle authentication from any supported platform through a single, cohesive solution. It maintains the necessary mappings between platform-specific identities and the internal account structure of Amazon Game Studios.
Results
As a result of developing and implementing this solution, Amazon Game Studios was able to successfully support a large number of concurrent users (CCU) for games during both normal traffic periods and major launches. Examples of this from the Steam platform include ~1.3 million CCU for Lost Ark, ~913,000 CCU for New World: Aeternum, and ~336,000 CCU for Throne and Liberty.
The unified authentication solution has also made it quicker for Amazon Game Studios to conduct security and privacy reviews, particularly when needing to add a new authentication mechanism. Since all the changes needed to add a new authentication solution can be performed within a single place, other services are not needed to make changes, resulting in a reduced need for widespread security and privacy reviews.
Conclusion
The gaming industry’s fragmented landscape presented Amazon Game Studios with a significant challenge: Platforms lacked standardization in their authentication protocols, token formats, and security frameworks. This makes it difficult for developers to support players across multiple ecosystems.
However, Amazon Game Studios implemented a unified authentication solution that helped them to streamline the process of integrating with various game platforms by converting tokens into a standard JWT format. This resulted in a unifying authentication solution, with the power to automatically scale as needed to support large numbers of concurrent users during any type of usage.
Contact an AWS Representative to know how we can help accelerate your business.
Further reading
Author: Olivia Liddell


