
Integrate Kubernetes policy-as-code solutions into Security Hub
kubectl create -f https://github… To deploy the solution Clone the GitHub repository by using your preferred command line terminal: git clone https://github…Using Kubernetes policy-as-code (PaC) solutions, administrators and security professionals can enforce organization p…
Using Kubernetes policy-as-code (PaC) solutions, administrators and security professionals can enforce organization policies to Kubernetes resources. There are several publicly available PAC solutions that are available for Kubernetes, such as Gatekeeper, Polaris, and Kyverno.
PaC solutions usually implement two features:
- Use Kubernetes admission controllers to validate or modify objects before they’re created to help enforce configuration best practices for your clusters.
- Provide a way for you to scan your resources created before policies were deployed or against new policies being evaluated.
This post presents a solution to send policy violations from PaC solutions using Kubernetes policy report format (for example, using Kyverno) or from Gatekeeper’s constraints status directly to AWS Security Hub. With this solution, you can visualize Kubernetes security misconfigurations across your Amazon Elastic Kubernetes Service (Amazon EKS) clusters and your organizations in AWS Organizations. This can also help you implement standard security use cases—such as unified security reporting, escalation through a ticketing system, or automated remediation—on top of Security Hub to help improve your overall Kubernetes security posture and reduce manual efforts.
Solution overview
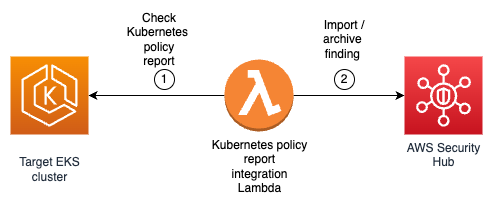
The solution uses the approach described in A Container-Free Way to Configure Kubernetes Using AWS Lambda to deploy an AWS Lambda function that periodically synchronizes the security status of a Kubernetes cluster from a Kubernetes or Gatekeeper policy report with Security Hub. Figure 1 shows the architecture diagram for the solution.

Figure 1: Diagram of solution
This solution works using the following resources and configurations:
- A scheduled event which invokes a Lambda function on a 10-minute interval.
- The Lambda function iterates through each running EKS cluster that you want to integrate and authenticate by using a Kubernetes Python client and an AWS Identity and Access Management (IAM) role of the Lambda function.
- For each running cluster, the Lambda function retrieves the selected Kubernetes policy reports (or the Gatekeeper constraint status, depending on the policy selected) and sends active violations, if present, to Security Hub. With Gatekeeper, if more violations exist than those reported in the constraint, an additional INFORMATIONAL finding is generated in Security Hub to let security teams know of the missing findings.
Optional: EKS cluster administrators can raise the limit of reported policy violations by using the
–constraint-violations-limitflag in their Gatekeeper audit operation. - For each running cluster, the Lambda function archives archive previously raised and resolved findings in Security Hub.
You can download the solution from this GitHub repository.
Walkthrough
In the walkthrough, I show you how to deploy a Kubernetes policy-as-code solution and forward the findings to Security Hub. We’ll configure Kyverno and a Kubernetes demo environment with findings in an existing EKS cluster to Security Hub.
The code provided includes an example constraint and noncompliant resource to test against.
Prerequisites
An EKS cluster is required to set up this solution within your AWS environments. The cluster should be configured with either aws-auth ConfigMap or access entries. Optional: You can use eksctl to create a cluster.
The following resources need to be installed on your computer:
- Git command line interface.
- Bash shell. On Windows 10, you can install the Windows Subsystem for Linux
- AWS Command Line Interface (AWS CLI)
- eksctl and Kubectl
- Python3 and pip
Step 1: Set up the environment
The first step is to install Kyverno on an existing Kubernetes cluster. Then deploy examples of a Kyverno policy and noncompliant resources.
Deploy Kyverno example and policy
- Deploy Kyverno in your Kubernetes cluster according to its installation manual using the Kubernetes CLI.
- Set up a policy that requires namespaces to use the label thisshouldntexist.
Deploy a noncompliant resource to test this solution
- Create a noncompliant namespace.
- Check the Kubernetes policy report status using the following command:
You should see output similar to the following:
Step 2: Solution code deployment and configuration
The next step is to clone and deploy the solution that integrates with Security Hub.
To deploy the solution
- Clone the GitHub repository by using your preferred command line terminal:
- Open the parameters.json file and configure the following values:
- Policy – Name of the product that you want to enable, in this case policyreport, which is supported by tools such as Kyverno.
- ClusterNames – List of EKS clusters. When AccessEntryEnabled is enabled, this solution deploys an access entry for the integration to access your EKS clusters.
- SubnetIds – (Optional) A comma-separated list of your subnets. If you’ve configured the API endpoints of your EKS clusters as private only, then you need to configure this parameter. If your EKS clusters have public endpoints enabled, you can remove this parameter.
- SecurityGroupId – (Optional) A security group ID that allows connectivity to the EKS clusters. This parameter is only required if you’re running private API endpoints; otherwise, you can remove it. This security group should be allowed ingress from the security group of the EKS control plane.
- AccessEntryEnabled – (Optional) If you’re using EKS access entries, the solution automatically deploys the access entries with read-only-group permissions deployed in the next step. This parameter is True by default.
- Save the changes and close the parameters file.
- Set up your AWS_REGION (for example, export AWS_REGION=eu-west-1) and make sure that your credentials are configured for the delegated administrator account.
- Enter the following command to deploy:
You should see the following output:
Step 3: Set up EKS cluster access
You need to create the Kubernetes Group read-only-group to allow read-only permissions to the IAM role of the Lambda function. If you aren’t using access entries, you will also need to modify the aws-auth ConfigMap of the Kubernetes clusters.
To configure access to EKS clusters
- For each cluster that’s running in your account, run the kube-setup.sh script to create the Kubernetes read-only cluster role and cluster role binding.
- (Optional) Configure aws-auth ConfigMap using eksctl if you aren’t using access entries.
Step 4: Verify AWS service integration
The next step is to verify that the Lambda integration to Security Hub is running.
To verify the integration is running
- Open the Lambda console, and navigate to the aws-securityhub-k8s-policy-integration-<region> function.
- Start a test to import your cluster’s noncompliant findings to Security Hub.
- In the Security Hub console, review the recently created findings from Kyverno.

Figure 2: Sample Kyverno findings in Security Hub
Step 5: Clean up
The final step is to clean up the resources that you created for this walkthrough.
To destroy the stack
- Use the command line terminal in your laptop to run the following command:
Conclusion
In this post, you learned how to integrate Kubernetes policy report findings with Security Hub and tested this setup by using the Kyverno policy engine. If you want to test the integration of this solution with Gatekeeper, you can find alternative commands for step 1 of this post in the GitHub repository’s README file.
Using this integration, you can gain visibility into your Kubernetes security posture across EKS clusters and join it with a centralized view, together with other security findings such as those from AWS Config, Amazon Inspector, and more across your organization. You can also try this solution with other tools, such as kube-bench or Gatekeeper. You can extend this setup to notify security teams of critical misconfigurations or implement automated remediation actions by using AWS Security Hub.
For more information on how to use PaC solutions to secure Kubernetes workloads in the AWS cloud, see Amazon Elastic Kubernetes Service (Amazon EKS) workshop, Amazon EKS best practices, Using Gatekeeper as a drop-in Pod Security Policy replacement in Amazon EKS and Policy-based countermeasures for Kubernetes.
If you have feedback about this post, submit comments in the Comments section below. If you have questions about this post, contact AWS Support.
Author: Joaquin Manuel Rinaudo

