
Introducing the AWS Zero Trust Accelerator for Government
Traditional perimeter-based security models—which rely on the assumption of trust within an organization’s network boundaries—are no longer sufficient… This executive order mandates US federal agencies to adopt zero trust architectures (ZTAs) to strengthen their cybersecurity posture and pr…
Government agencies face an unprecedented challenge when designing security against unauthorized access to IT infrastructure and data. Traditional perimeter-based security models—which rely on the assumption of trust within an organization’s network boundaries—are no longer sufficient. The wide adoption of bring-your-own-device (BYOD) and cloud-based resources requires adopting additional security measures beyond the traditional perimeter-based models. High-profile cyber incidents, such as the Global exploit of the JetBrains CVE and the compromise of federal networks by Iranian government-sponsored APT actors, highlight the limitations of traditional perimeter-based security models.
Recognizing the urgency of this challenge, the Biden administration issued Executive Order 14028, “Improving the Nation’s Cybersecurity,” in May 2021. This executive order mandates US federal agencies to adopt zero trust architectures (ZTAs) to strengthen their cybersecurity posture and protect critical infrastructure from cyber threats. Additionally, the Department of Defense (DoD) and the Cybersecurity and Infrastructure Security Agency (CISA) have published comprehensive guidance on implementing zero trust principles, including the DoD Zero Trust Strategy and the CISA Zero Trust Maturity Model. The US Office of Management and Budget (OMB) has set targets for Federal Civilian Executive Branch (FCEB) agencies to implement CISA guidance in FY2024 and FY2025, while DoD has set targets for FY2027 and beyond.
Zero trust principles focus on authorizing access to protected resources such as data, applications, and services, by continuously verifying the identity and security posture of every user, device, and transaction, regardless of network location. This approach aims to reduce the concept of implicit trust, verifying that only authorized entities gain access to sensitive resources and reducing the risks associated with unauthorized access and lateral movement within the network.
Amazon Web Services (AWS) is at the forefront of this paradigm shift, offering a government-centric suite of services and capabilities to support government agencies in their transition to a zero trust approach. The zero trust approach recommended by AWS is designed to provide a robust, scalable, and forward-looking cybersecurity strategy that aligns with government mandates and empowers agencies to secure their mission-critical resources effectively.
The AWS ZTAG: A government-centric approach
The AWS Zero Trust Accelerator for Government (ZTAG) is a government-centric set of resources to help government organizations implement zero trust architectures. ZTAG encompasses several accelerators, including:
- Zero trust maturity assessment tools
- Reference architectures and implementation guidance
- Integration of AWS services and AWS Independent Software Vendor (ISV) partner solutions
- AWS ISV reference implementations with industry-leading ISV partners
- A streamlined procurement process through AWS Marketplace
The ZTAG assessment tools help you identify gaps in adhering to government zero trust requirements and provide tailored guidance and recommendations. This includes AWS services and AWS ISV partner solutions designed to help you achieve specific US DoD zero trust activities or CISA zero trust functions. ZTAG is initially focused on US government zero trust frameworks with applicability at the federal, state, and local levels, with adoption of international zero trust frameworks on the roadmap.
Accelerating zero trust adoption with AWS
The ZTAG approach is specifically tailored to help meet the unique requirements and challenges faced by government agencies, offering several key benefits:
- Aligns with US DoD and CISA zero trust models and is extensible to other government or industry models as they emerge
- Accelerates your journey to a secure and resilient IT infrastructure by helping you identify zero trust gaps and define roadmaps to achieve cybersecurity objectives
- Starts with your existing cyber capabilities and extends them as needed with best-of-breed AWS ISV partners
- Incremental approach to adoption enables smooth transition to a zero trust architecture
- Dedicated expertise to assist government agencies throughout their zero trust journey
Getting started with ZTAG
To get started with their zero trust journey, government agencies can use AWS zero trust assessments, tailored to the DoD or CISA frameworks. Work with a dedicated zero trust specialist to complete an assessment of your current environment. These assessments help you identify your agency’s current zero trust maturity level, pinpoint gaps, and develop a customized roadmap aligned with your specific requirements and budgets. You can reassess your environment at any time to track progress over time.

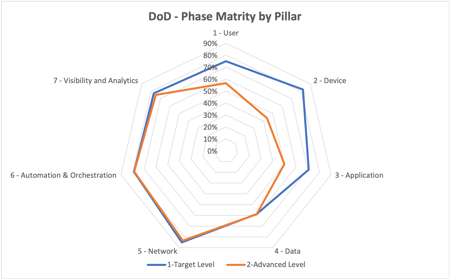
Figure 1: Example of DoD phase maturity by pillar

Figure 2: Example of DoD phase activities by maturity level
Conclusion
The AWS Zero Trust Accelerator for Government (ZTAG) represents the commitment made by AWS to support US federal agencies in their transition to zero trust architectures. By combining the AWS Cloud infrastructure with industry-leading security solutions, ZTAG provides a government-centric and flexible approach to achieving a robust cybersecurity posture while maintaining operational agility.
Government agencies can use ZTAG to accelerate their zero trust adoption, enhance their overall security posture, and align with critical compliance requirements. Contact your AWS account team to learn more about how AWS can support your agency’s zero trust journey.
If you have feedback about this post, submit comments in the Comments section below.
Author: Derek Doerr
