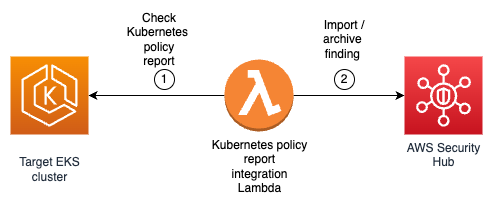
Integrate Kubernetes policy-as-code solutions into Security Hub
TutoSartup excerpt from this article:
kubectl create -f https://github... To deploy the solution Clone the GitHub repository by using your preferred command line terminal: git clone https://github...Using Kubernetes policy-as-code (PaC) solutions, administrators and security professionals can enforce organization policies to Kubernetes resources... This post presents a solution to send policy violations from P...
kubectl create -f https://github... To deploy the solution Clone the GitHub repository by using your preferred command line terminal: git clone https://github...Using Kubernetes policy-as-code (PaC) solutions, administrators and security professionals can enforce organization policies to Kubernetes resources... This post presents a solution to send policy violations from P...
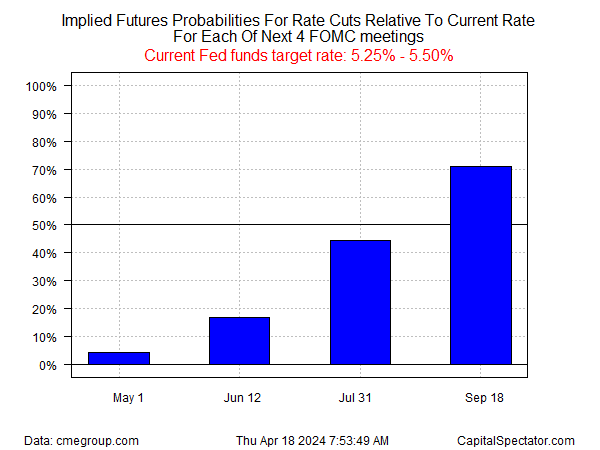
Rate-Cut Forecast Now Seen For September At Earliest
TutoSartup excerpt from this article:
Fed funds futures this morning (Apr... With the inflation data exceeding expectations to start the year, it comes as little surprise that the Fed would push back on any urgency to cut, especially given the strong activity data...0% range, the 2-year rate appears to be waiting for the next round of inflation data before making a sharp move one way or the other...The next major ...
Fed funds futures this morning (Apr... With the inflation data exceeding expectations to start the year, it comes as little surprise that the Fed would push back on any urgency to cut, especially given the strong activity data...0% range, the 2-year rate appears to be waiting for the next round of inflation data before making a sharp move one way or the other...The next major ...
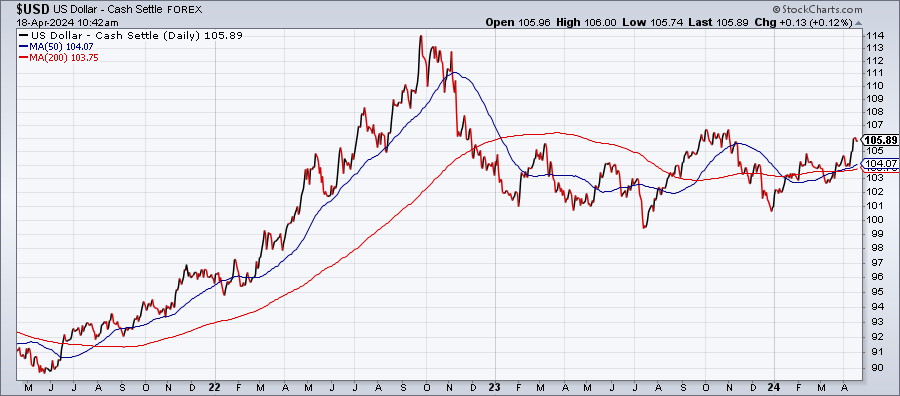
Macro Briefing: 18 April 2024
TutoSartup excerpt from this article:
* Some economists now see rate cuts delayed until March 2025, * Fed’s Beige Book reports steady economic growth but slim progress on inflation * ‘Insatiable’ AI demand expected to lift Q2 sales for world’s biggest chipmaker * Climate change bill may reach $38 trillion a year by 2049, study finds * US dollar’s dominant reserve currency status likely to endure: Morgan StanleyUS debt is ...
* Some economists now see rate cuts delayed until March 2025, * Fed’s Beige Book reports steady economic growth but slim progress on inflation * ‘Insatiable’ AI demand expected to lift Q2 sales for world’s biggest chipmaker * Climate change bill may reach $38 trillion a year by 2049, study finds * US dollar’s dominant reserve currency status likely to endure: Morgan StanleyUS debt is ...

How the unique culture of security at AWS makes a difference
TutoSartup excerpt from this article:
They choose us because security has been our top priority from day one... We designed AWS from its foundation to be the most secure way for our customers to run their workloads, and we’ve built our internal culture around security as a business imperative... While technical security measures are important, organizations are made up of people... A recent report from the Cyber Safety Review Boar...
They choose us because security has been our top priority from day one... We designed AWS from its foundation to be the most secure way for our customers to run their workloads, and we’ve built our internal culture around security as a business imperative... While technical security measures are important, organizations are made up of people... A recent report from the Cyber Safety Review Boar...
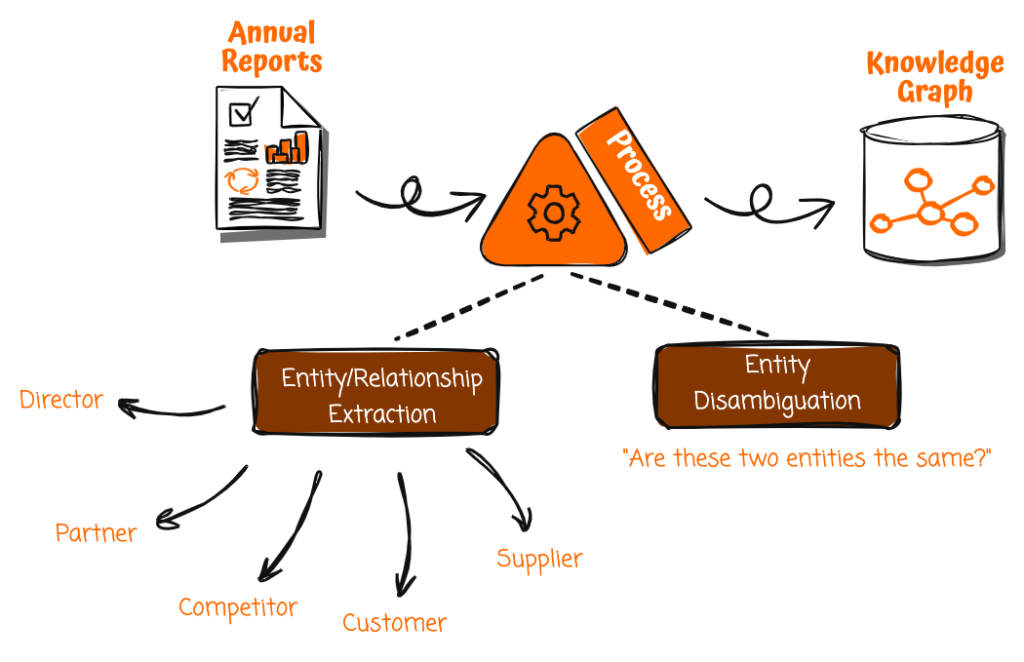
Uncover hidden connections in unstructured financial data with Amazon Bedrock and Amazon Neptune
TutoSartup excerpt from this article:
In this post, we demonstrate an automated solution combining knowledge graphs and generative artificial intelligence (AI) to surface such risks by cross-referencing relationship maps with real-time news... Broadly, this entails two steps: First, building the intricate relationships between companies (customers, suppliers, directors) into a knowledge graph... Second, using this graph database alo...
In this post, we demonstrate an automated solution combining knowledge graphs and generative artificial intelligence (AI) to surface such risks by cross-referencing relationship maps with real-time news... Broadly, this entails two steps: First, building the intricate relationships between companies (customers, suppliers, directors) into a knowledge graph... Second, using this graph database alo...

Azure IoT’s industrial transformation strategy on display at Hannover Messe 2024
TutoSartup excerpt from this article:
Azure IoT Operations Build interoperable IoT solutions that transform physical operations at scale Discover solutions accelerating industrial transformation with azure iot operations Read the blogWe will be demonstrating these ...
Azure IoT Operations Build interoperable IoT solutions that transform physical operations at scale Discover solutions accelerating industrial transformation with azure iot operations Read the blogWe will be demonstrating these ...

Open source observability for AWS Inferentia nodes within Amazon EKS clusters
TutoSartup excerpt from this article:
892000-04:00", "name": "accelerator-workspace", "notificationDestinations": [ "SNS" ], "status": "ACTIVE", "tags": {} } ] } Assign the values of id and endpoint to the following environment variables: export COA_AMG_WORKSPACE_ID="<<YOUR-WORKSPACE-ID, similar to the above g-XYZ, without quotation marks>>" export COA_AMG_ENDPOINT_UR...
892000-04:00", "name": "accelerator-workspace", "notificationDestinations": [ "SNS" ], "status": "ACTIVE", "tags": {} } ] } Assign the values of id and endpoint to the following environment variables: export COA_AMG_WORKSPACE_ID="<<YOUR-WORKSPACE-ID, similar to the above g-XYZ, without quotation marks>>" export COA_AMG_ENDPOINT_UR...
