
2024 ISO and CSA STAR certificates now available with two additional AWS Regions and three additional services
TutoSartup excerpt from this article:
The objective of the audit was to assess the level of compliance with the requirements of the applicable international standards... During this special onboarding, we added two additional AWS Regions (Israel (Tel Aviv)) and Canada West (Calgary)) and three additional AWS services to the scope since the last certification issued on Nov 22, 2023... Customers can also access the certifications in t...
The objective of the audit was to assess the level of compliance with the requirements of the applicable international standards... During this special onboarding, we added two additional AWS Regions (Israel (Tel Aviv)) and Canada West (Calgary)) and three additional AWS services to the scope since the last certification issued on Nov 22, 2023... Customers can also access the certifications in t...

AWS Weekly Roundup – Application Load Balancer IPv6, Amazon S3 pricing update, Amazon EC2 Flex instances, and more (May 20, 2024)
TutoSartup excerpt from this article:
AWS Summit season is in full swing around the world, with last week’s events in Bengaluru, Berlin, and Seoul, where my blog colleague Channy delivered one of the keynotes... Amazon EventBridge now supports customer managed keys (CMK) for event buses – This capability allows you to encrypt your events using your own keys instead of an AWS owned key (which is used by default)... With support ...
AWS Summit season is in full swing around the world, with last week’s events in Bengaluru, Berlin, and Seoul, where my blog colleague Channy delivered one of the keynotes... Amazon EventBridge now supports customer managed keys (CMK) for event buses – This capability allows you to encrypt your events using your own keys instead of an AWS owned key (which is used by default)... With support ...
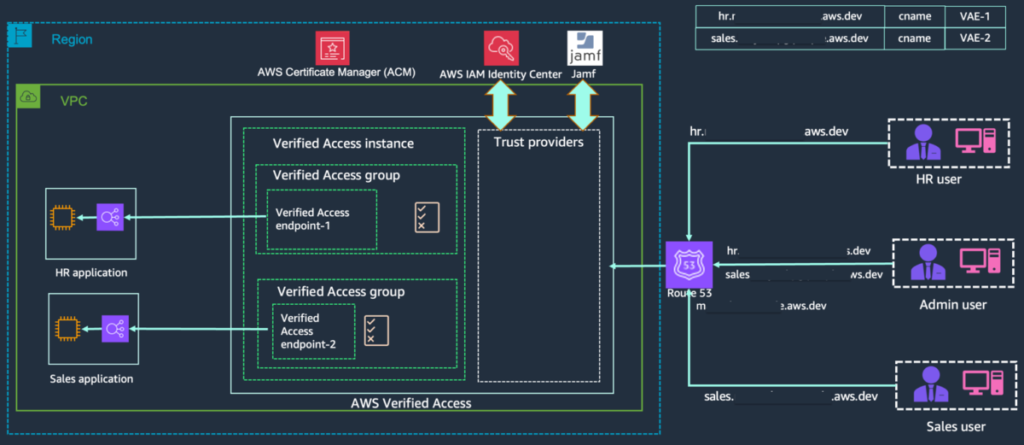
Integrating AWS Verified Access with Jamf as a device trust provider
TutoSartup excerpt from this article:
Specifically, we show you how to integrate AWS Verified Access with Jamf as a device trust provider... This post is an extension of our previous post explaining how to integrate AWS Verified Access with CrowdStrike... In this post, we also look at how to troubleshoot Verified Access policies and integration issues for when a user with valid access receives access denied or unauthorized error mess...
Specifically, we show you how to integrate AWS Verified Access with Jamf as a device trust provider... This post is an extension of our previous post explaining how to integrate AWS Verified Access with CrowdStrike... In this post, we also look at how to troubleshoot Verified Access policies and integration issues for when a user with valid access receives access denied or unauthorized error mess...
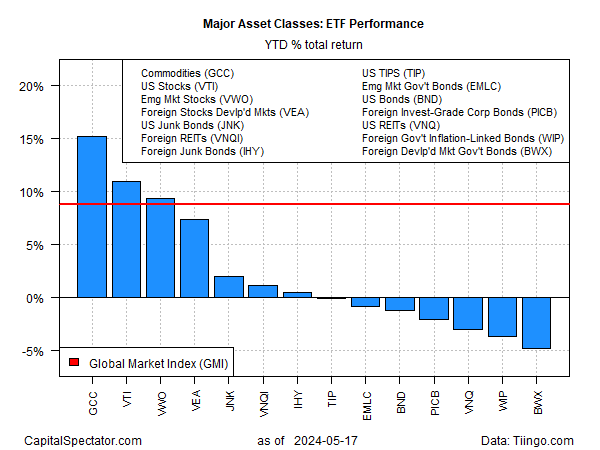
Commodities’ Performance Lead Widens Over Markets In 2024
TutoSartup excerpt from this article:
Last week’s strong rally in commodities expanded the performance lead for the asset class over the rest of global markets, based on a set of ETFs through Friday’s close (May 17)...4% this year, more than four percentage points above the year-to-date rise for US stocks (VTI), the second-best performer for the major asset classes in 2024 via an 11...Several bullish trends have helped drive key...
Last week’s strong rally in commodities expanded the performance lead for the asset class over the rest of global markets, based on a set of ETFs through Friday’s close (May 17)...4% this year, more than four percentage points above the year-to-date rise for US stocks (VTI), the second-best performer for the major asset classes in 2024 via an 11...Several bullish trends have helped drive key...
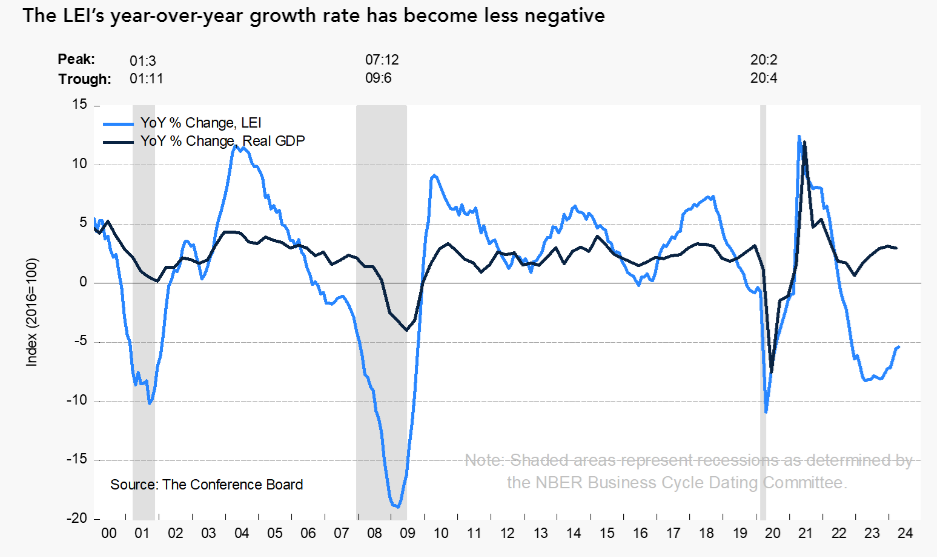
Macro Briefing: 20 May 2024
TutoSartup excerpt from this article:
* Iran’s president dies in helicopter crash * Gold rises to record high in early Monday trading * Copper hits record high in anticipation of deepening supply shortages * Do the new Biden tariffs mark the end of cheap Chinese goods for US? * US Leading Economic stays negative in April as growth persists:The Congressional Budget Office, which reports on the nation’s fiscal condition, projects...
* Iran’s president dies in helicopter crash * Gold rises to record high in early Monday trading * Copper hits record high in anticipation of deepening supply shortages * Do the new Biden tariffs mark the end of cheap Chinese goods for US? * US Leading Economic stays negative in April as growth persists:The Congressional Budget Office, which reports on the nation’s fiscal condition, projects...

Book Bits: 18 May 2024
TutoSartup excerpt from this article:
By purchasing books through this site, you provide support for The Capital Spectator’s free content...● A Map of the New Normal: How Inflation, War, and Sanctions Will Change Your World Forever Jeff Rubin Adapted essay from book via The Globe and Mail The world is engulfed in an ever-escalating global trade war... Where will this lead? Can the West still win such wars, as it has done before? ...
By purchasing books through this site, you provide support for The Capital Spectator’s free content...● A Map of the New Normal: How Inflation, War, and Sanctions Will Change Your World Forever Jeff Rubin Adapted essay from book via The Globe and Mail The world is engulfed in an ever-escalating global trade war... Where will this lead? Can the West still win such wars, as it has done before? ...

5 ways to increase AWS Certified employees in your organization
TutoSartup excerpt from this article:
Did you know that 95% of customers consider cloud certifications important in their decision-making process when choosing an AWS Partner? Moreover, 85% cite them as a deciding factor when selecting a partner (Canalys, 2023)... Customers can trust that certified partners have undergone rigorous training and assessments, validating their expertise and commitment to AWS technologies... While pursuin...
Did you know that 95% of customers consider cloud certifications important in their decision-making process when choosing an AWS Partner? Moreover, 85% cite them as a deciding factor when selecting a partner (Canalys, 2023)... Customers can trust that certified partners have undergone rigorous training and assessments, validating their expertise and commitment to AWS technologies... While pursuin...
