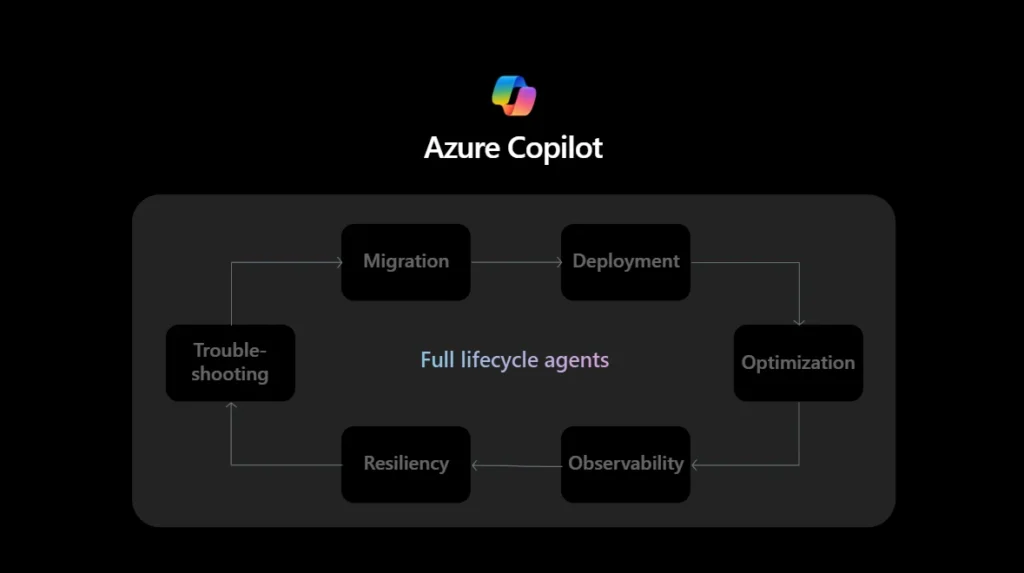
Agentic cloud operations: A new way to run the cloud
TutoSartup excerpt from this article:
See how you can run agents with Azure CopilotAs modern applications and AI workloads expand in scale, speed, and interconnectedness, operational demands are evolving just as quickly... At the same time, AI agents are emerging as practical operational partners—able to correlate signals, understand context, and take action within defined guardrails...Introducing agentic cloud operati...
See how you can run agents with Azure CopilotAs modern applications and AI workloads expand in scale, speed, and interconnectedness, operational demands are evolving just as quickly... At the same time, AI agents are emerging as practical operational partners—able to correlate signals, understand context, and take action within defined guardrails...Introducing agentic cloud operati...
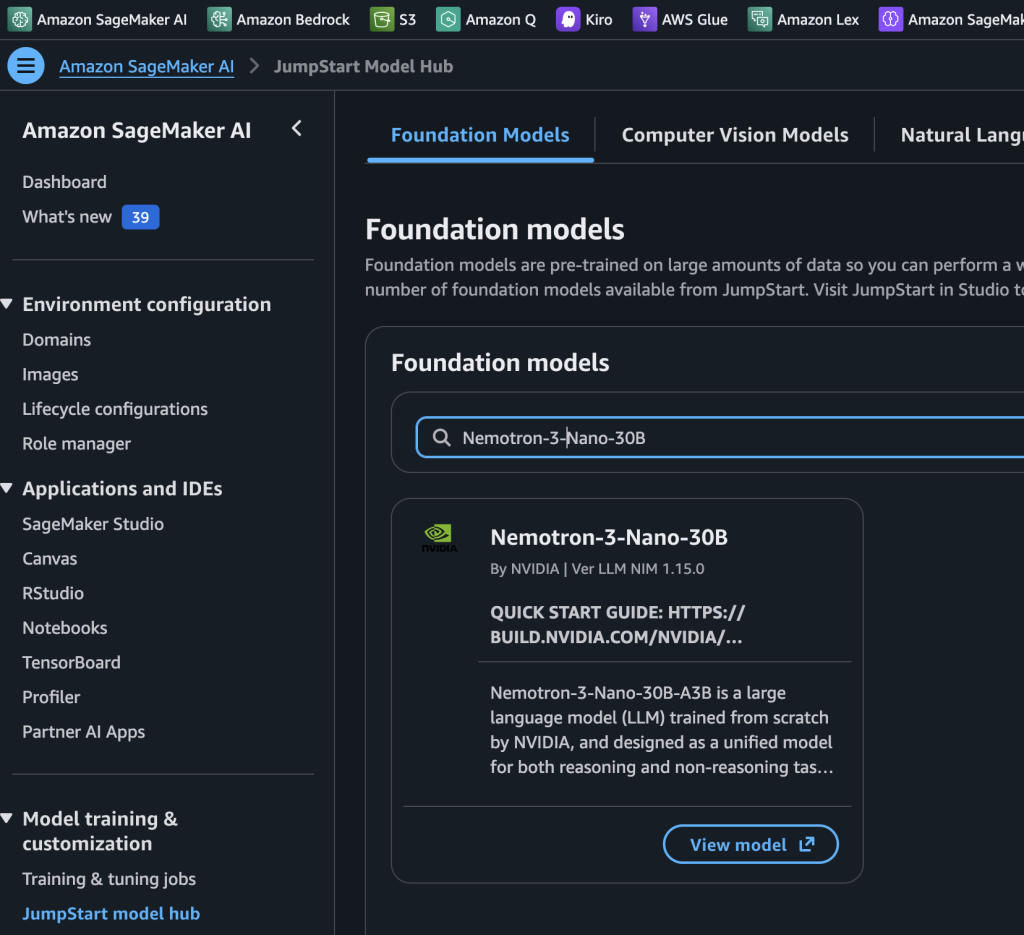
NVIDIA Nemotron 3 Nano 30B MoE model is now available in Amazon SageMaker JumpStart
TutoSartup excerpt from this article:
Today we’re excited to announce that the NVIDIA Nemotron 3 Nano 30B model with 3B active parameters is now generally available in the Amazon SageMaker JumpStart model catalog... You can accelerate innovation and deliver tangible business value with Nemotron 3 Nano on Amazon Web Services (AWS) without having to manage model deployment complexities... Nemotron 3 Nano is a small language hybrid ...
Today we’re excited to announce that the NVIDIA Nemotron 3 Nano 30B model with 3B active parameters is now generally available in the Amazon SageMaker JumpStart model catalog... You can accelerate innovation and deliver tangible business value with Nemotron 3 Nano on Amazon Web Services (AWS) without having to manage model deployment complexities... Nemotron 3 Nano is a small language hybrid ...
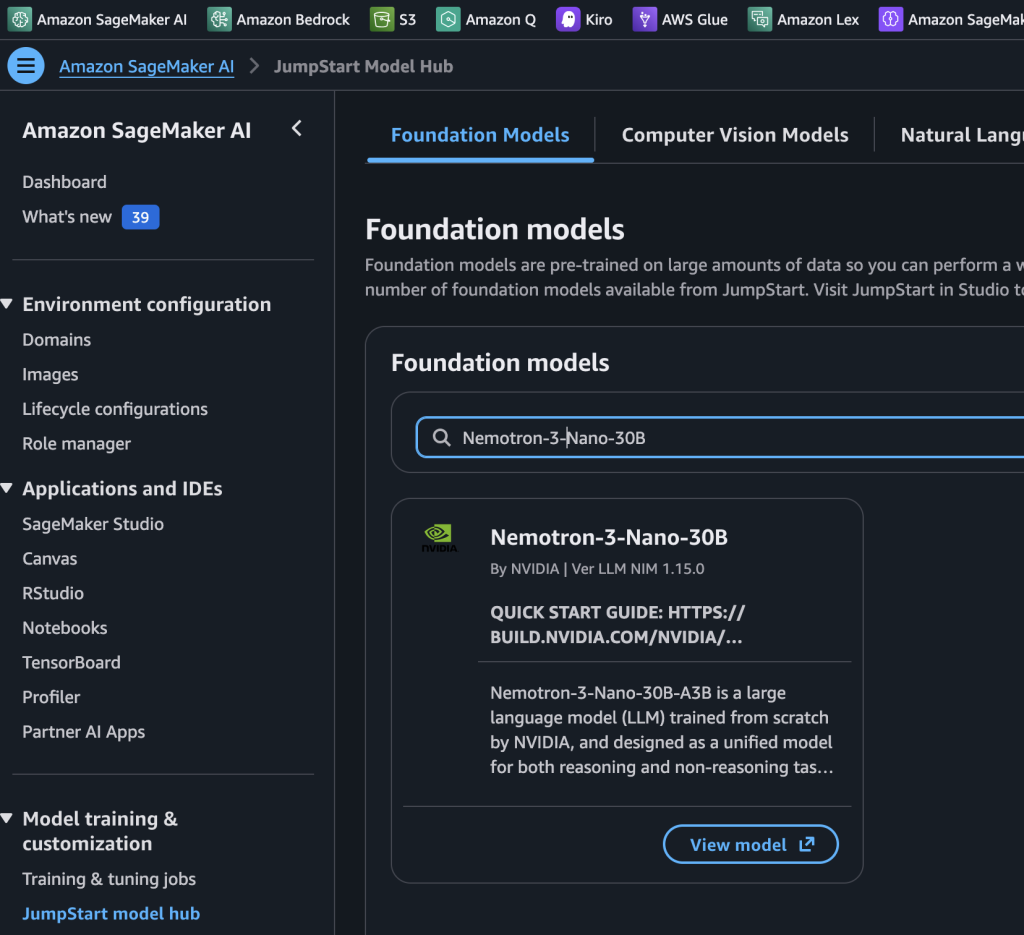
NVIDIA Nemotron 3 Nano 30B MoE model is now available in Amazon SageMaker JumpStart
TutoSartup excerpt from this article:
Today we’re excited to announce that the NVIDIA Nemotron 3 Nano 30B model with 3B active parameters is now generally available in the Amazon SageMaker JumpStart model catalog... You can accelerate innovation and deliver tangible business value with Nemotron 3 Nano on Amazon Web Services (AWS) without having to manage model deployment complexities... Nemotron 3 Nano is a small language hybrid ...
Today we’re excited to announce that the NVIDIA Nemotron 3 Nano 30B model with 3B active parameters is now generally available in the Amazon SageMaker JumpStart model catalog... You can accelerate innovation and deliver tangible business value with Nemotron 3 Nano on Amazon Web Services (AWS) without having to manage model deployment complexities... Nemotron 3 Nano is a small language hybrid ...

Mastering Amazon Bedrock throttling and service availability: A comprehensive guide
TutoSartup excerpt from this article:
By combining quota-aware design, intelligent retries, client-side resilience patterns, cross-Region strategies, and strong observability, you can keep your applications responsive even under unpredictable load... With a strong background in ML, he has three years of experience building AI applications and specializes in hardware inference optimizations for LLM models...In production generative AI...
By combining quota-aware design, intelligent retries, client-side resilience patterns, cross-Region strategies, and strong observability, you can keep your applications responsive even under unpredictable load... With a strong background in ML, he has three years of experience building AI applications and specializes in hardware inference optimizations for LLM models...In production generative AI...

Mastering Amazon Bedrock throttling and service availability: A comprehensive guide
TutoSartup excerpt from this article:
By combining quota-aware design, intelligent retries, client-side resilience patterns, cross-Region strategies, and strong observability, you can keep your applications responsive even under unpredictable load... With a strong background in ML, he has three years of experience building AI applications and specializes in hardware inference optimizations for LLM models...In production generative AI...
By combining quota-aware design, intelligent retries, client-side resilience patterns, cross-Region strategies, and strong observability, you can keep your applications responsive even under unpredictable load... With a strong background in ML, he has three years of experience building AI applications and specializes in hardware inference optimizations for LLM models...In production generative AI...
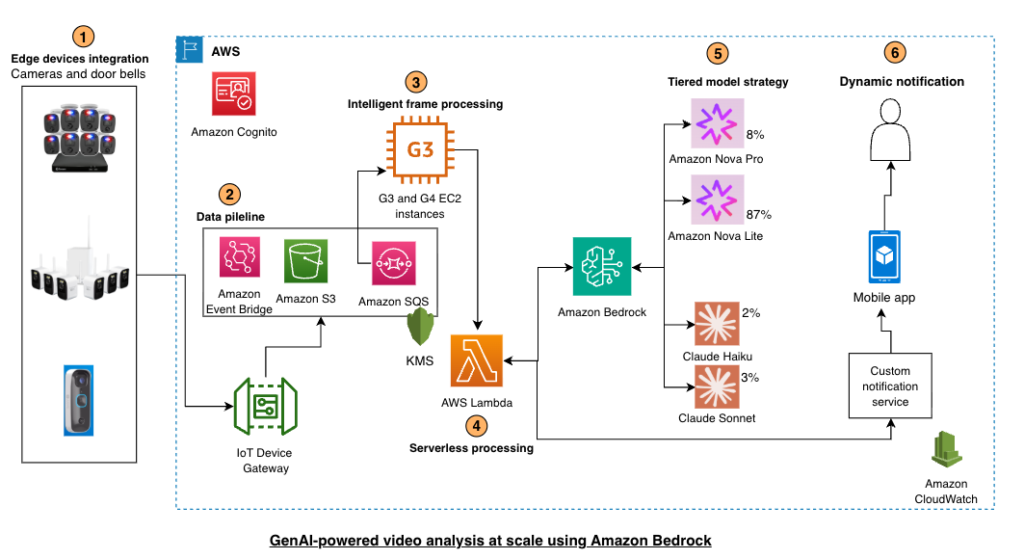
Swann provides Generative AI to millions of IoT Devices using Amazon Bedrock
TutoSartup excerpt from this article:
You’ll learn model selection strategies, cost optimization techniques, and architectural patterns for deploying gen-AI at IoT scale, based on Swann Communications deployment across millions of devices... As a pioneer in do-it-yourself (DIY) security solutions, Swann Communications has built a global network of more than 11... Swann partnered with Amazon Web Services (AWS) to develop a multi-mo...
You’ll learn model selection strategies, cost optimization techniques, and architectural patterns for deploying gen-AI at IoT scale, based on Swann Communications deployment across millions of devices... As a pioneer in do-it-yourself (DIY) security solutions, Swann Communications has built a global network of more than 11... Swann partnered with Amazon Web Services (AWS) to develop a multi-mo...
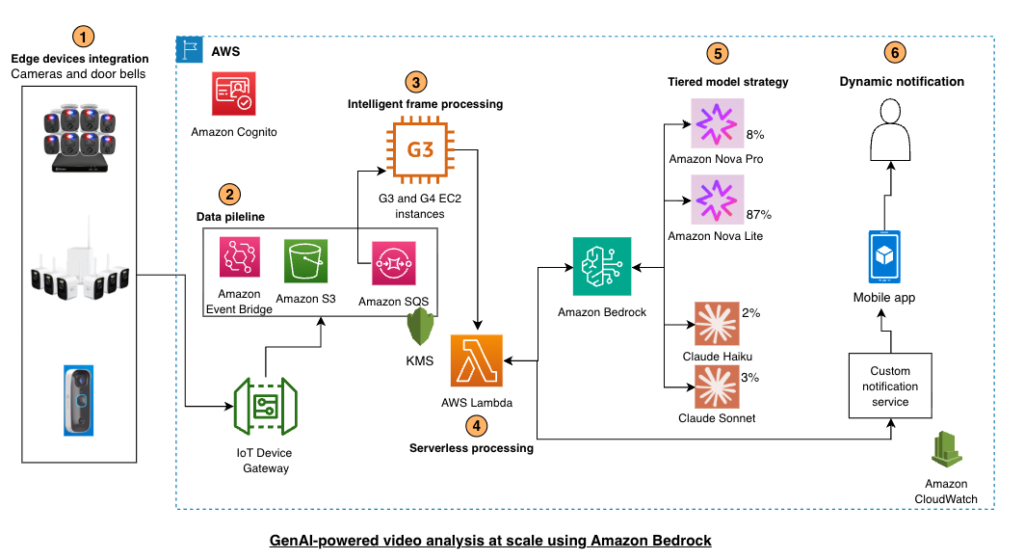
Swann provides Generative AI to millions of IoT Devices using Amazon Bedrock
TutoSartup excerpt from this article:
You’ll learn model selection strategies, cost optimization techniques, and architectural patterns for deploying gen-AI at IoT scale, based on Swann Communications deployment across millions of devices... As a pioneer in do-it-yourself (DIY) security solutions, Swann Communications has built a global network of more than 11... Swann partnered with Amazon Web Services (AWS) to develop a multi-mo...
You’ll learn model selection strategies, cost optimization techniques, and architectural patterns for deploying gen-AI at IoT scale, based on Swann Communications deployment across millions of devices... As a pioneer in do-it-yourself (DIY) security solutions, Swann Communications has built a global network of more than 11... Swann partnered with Amazon Web Services (AWS) to develop a multi-mo...
