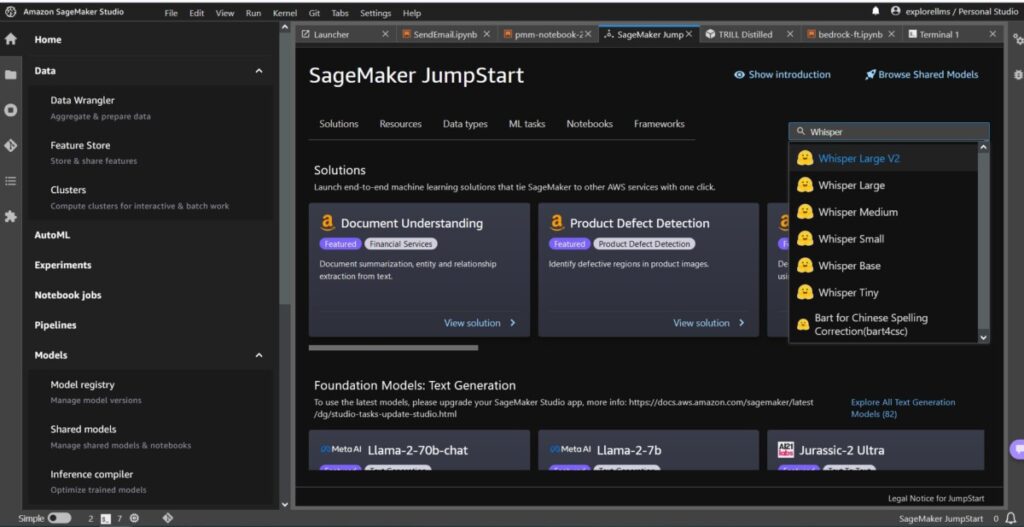
Whisper models for automatic speech recognition now available in Amazon SageMaker JumpStart
TutoSartup excerpt from this article:
Today, we’re excited to announce that the OpenAI Whisper foundation model is available for customers using Amazon SageMaker JumpStart... Whisper is a pre-trained model for automatic speech recognition (ASR) and speech translation... Trained on 680 thousand hours of labelled data, Whisper models demonstrate a strong ability to generalize to many datasets and domains without the need for fine-tun...
Today, we’re excited to announce that the OpenAI Whisper foundation model is available for customers using Amazon SageMaker JumpStart... Whisper is a pre-trained model for automatic speech recognition (ASR) and speech translation... Trained on 680 thousand hours of labelled data, Whisper models demonstrate a strong ability to generalize to many datasets and domains without the need for fine-tun...
Reinventing a cloud-native federated learning architecture on AWS
TutoSartup excerpt from this article:
Machine learning (ML), especially deep learning, requires a large amount of data for improving model performance... Customers often need to train a model with data from different regions, organizations, or AWS accounts... Federated learning (FL) is a distributed ML approach that trains ML models on distributed datasets... The goal of FL is to improve the accuracy of ML models by using more data, ...
Machine learning (ML), especially deep learning, requires a large amount of data for improving model performance... Customers often need to train a model with data from different regions, organizations, or AWS accounts... Federated learning (FL) is a distributed ML approach that trains ML models on distributed datasets... The goal of FL is to improve the accuracy of ML models by using more data, ...

Caroline Ellison blames Sam Bankman-Fried for misuse of FTX user funds at trial
TutoSartup excerpt from this article:
Reports have suggested the former CEO of Alameda Research and SBF had largely been out of contact following the collapse of FTX in November 2022... 10, Ellison admitted to fraud during her time at Alameda under Bankman-Fried’s direction... The former Alameda CEO reportedly placed the blame for misuse of FTX user funds directly on SBF, claiming he “set ...
Reports have suggested the former CEO of Alameda Research and SBF had largely been out of contact following the collapse of FTX in November 2022... 10, Ellison admitted to fraud during her time at Alameda under Bankman-Fried’s direction... The former Alameda CEO reportedly placed the blame for misuse of FTX user funds directly on SBF, claiming he “set ...
Microsoft empowers health organizations with generative AI and actionable data insights
TutoSartup excerpt from this article:
For the healthcare industry, this might mean the beginning of a transformative era that changes how healthcare is delivered and accessed—making precision medicine truly individualized, speeding up groundbreaking research for life threatening diseases, and finding new and innovative ways to improve patient care... Healthcare data has been growing at an exponential rate and most healthcare organi...
For the healthcare industry, this might mean the beginning of a transformative era that changes how healthcare is delivered and accessed—making precision medicine truly individualized, speeding up groundbreaking research for life threatening diseases, and finding new and innovative ways to improve patient care... Healthcare data has been growing at an exponential rate and most healthcare organi...
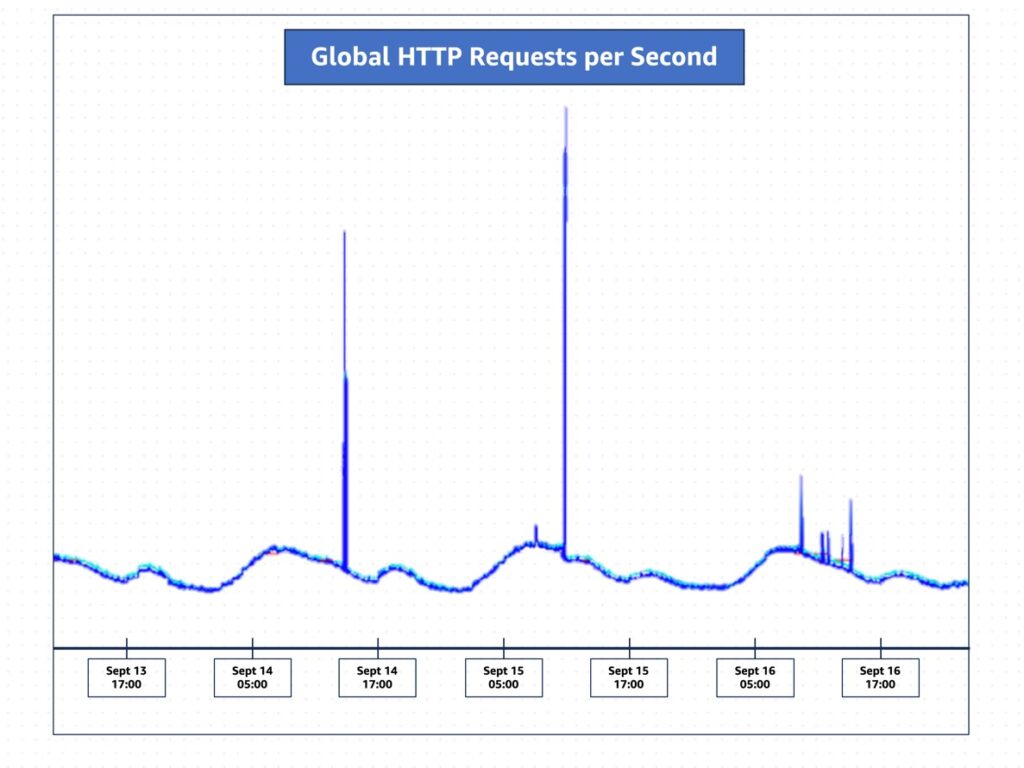
How AWS protects customers from DDoS events
TutoSartup excerpt from this article:
Examples of DDoS events include HTTP request floods, reflection/amplification attacks, and packet floods... The DDoS events AWS detected were a type of HTTP/2 request flood, which occurs when a high volume of illegitimate web requests overwhelms a web server’s ability to respond to legitimate client requests... Between August 28 and August 29, 2023, proactive monitoring by AWS detected an unus...
Examples of DDoS events include HTTP request floods, reflection/amplification attacks, and packet floods... The DDoS events AWS detected were a type of HTTP/2 request flood, which occurs when a high volume of illegitimate web requests overwhelms a web server’s ability to respond to legitimate client requests... Between August 28 and August 29, 2023, proactive monitoring by AWS detected an unus...
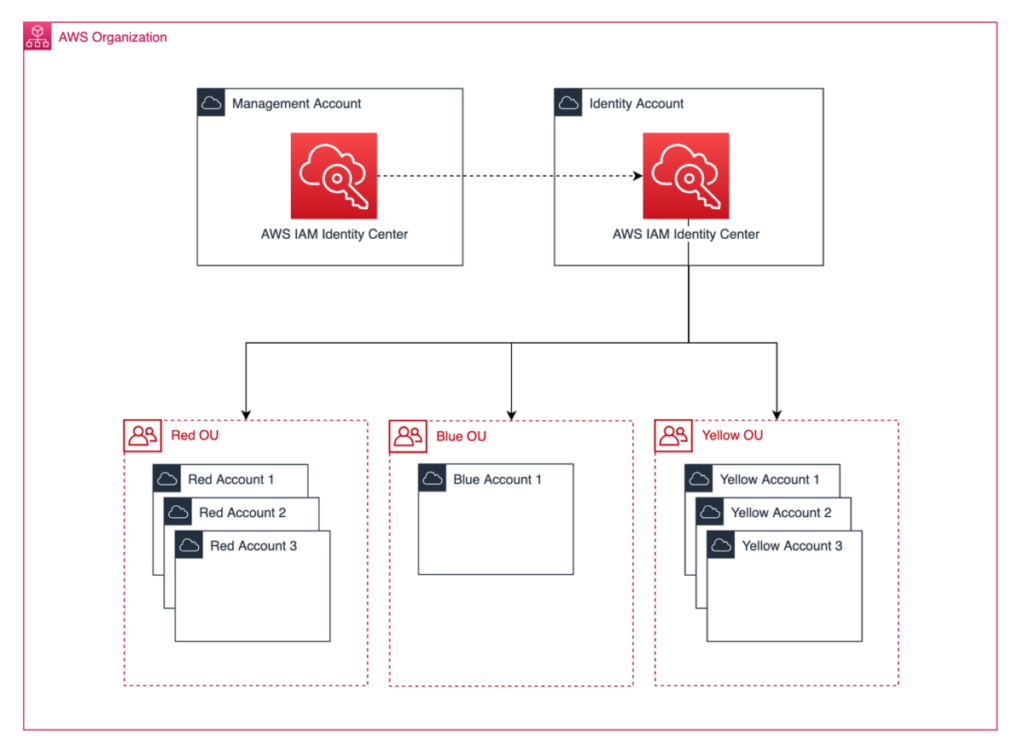
Delegating permission set management and account assignment in AWS IAM Identity Center
TutoSartup excerpt from this article:
In this blog post, we look at how you can use AWS IAM Identity Center (successor to AWS Single Sign-On) to delegate the management of permission sets and account assignments... Delegated administration is different from the delegation of permission sets and account assignments, which this blog covers... Permission sets can contain AWS managed policies, customer managed policies, inline policies, ...
In this blog post, we look at how you can use AWS IAM Identity Center (successor to AWS Single Sign-On) to delegate the management of permission sets and account assignments... Delegated administration is different from the delegation of permission sets and account assignments, which this blog covers... Permission sets can contain AWS managed policies, customer managed policies, inline policies, ...

AWS Weekly Roundup: AWS Control Tower, Amazon Bedrock, Amazon OpenSearch Service, and More (October 9, 2023)
TutoSartup excerpt from this article:
Last Week’s Launches Here are some launches that got my attention: AWS Control Tower – AWS Control Tower released 22 proactive controls and 10 AWS Security Hub detective controls to help you meet regulatory requirements and meet control objectives such as encrypting data in transit, encrypting data at rest, or using strong authentication... To get started building and scaling generative AI...
Last Week’s Launches Here are some launches that got my attention: AWS Control Tower – AWS Control Tower released 22 proactive controls and 10 AWS Security Hub detective controls to help you meet regulatory requirements and meet control objectives such as encrypting data in transit, encrypting data at rest, or using strong authentication... To get started building and scaling generative AI...
