
Sam Bankman-Fried’s brother planned to buy island and prep for apocalypse: court filing
TutoSartup excerpt from this article:
According to court documents, Gabriel Bankman-Fried wrote a memo to the FTX Foundation with a plan to build a bunker to survive “some event where 50%-99... Gabriel Bankman-Fried, the brother of former FTX CEO Sam Bankman-Fried, had a plan to survive a global catastrophe using funds from the now defunct cryptocurrency exchange...Accord...
According to court documents, Gabriel Bankman-Fried wrote a memo to the FTX Foundation with a plan to build a bunker to survive “some event where 50%-99... Gabriel Bankman-Fried, the brother of former FTX CEO Sam Bankman-Fried, had a plan to survive a global catastrophe using funds from the now defunct cryptocurrency exchange...Accord...
Analyze rodent infestation using Amazon SageMaker geospatial capabilities
TutoSartup excerpt from this article:
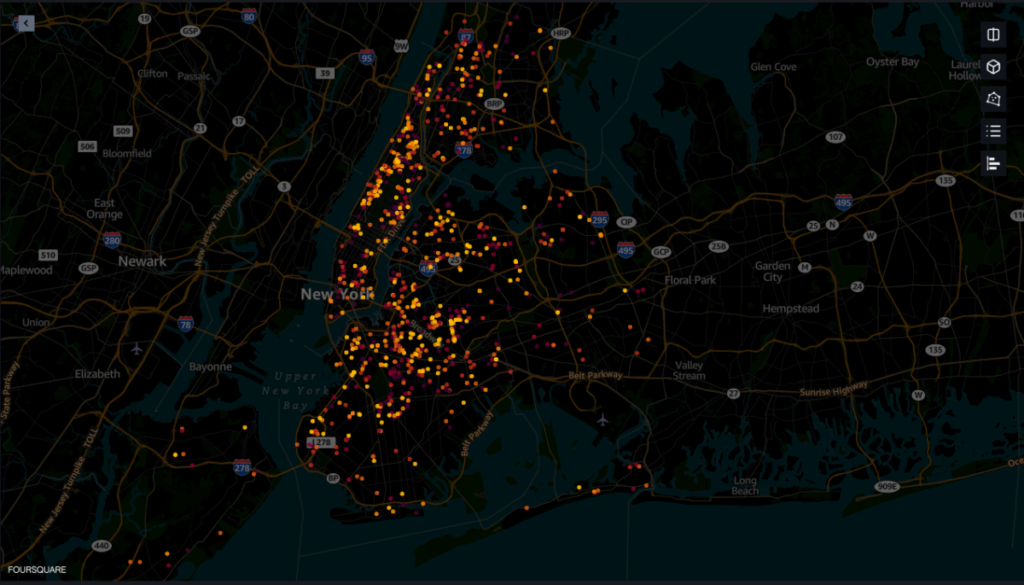
In this post, we show how to monitor and visualize a rodent population using Amazon SageMaker geospatial capabilities... Amazon SageMaker makes it easier for data scientists and machine learning (ML) engineers to build, train, and deploy models using geospatial data... The tool makes it easier to access geospatial data sources, run purpose-built processing operations, apply pre-trained ML models...
In this post, we show how to monitor and visualize a rodent population using Amazon SageMaker geospatial capabilities... Amazon SageMaker makes it easier for data scientists and machine learning (ML) engineers to build, train, and deploy models using geospatial data... The tool makes it easier to access geospatial data sources, run purpose-built processing operations, apply pre-trained ML models...
Migrating your secrets to AWS Secrets Manager, Part 2: Implementation
TutoSartup excerpt from this article:
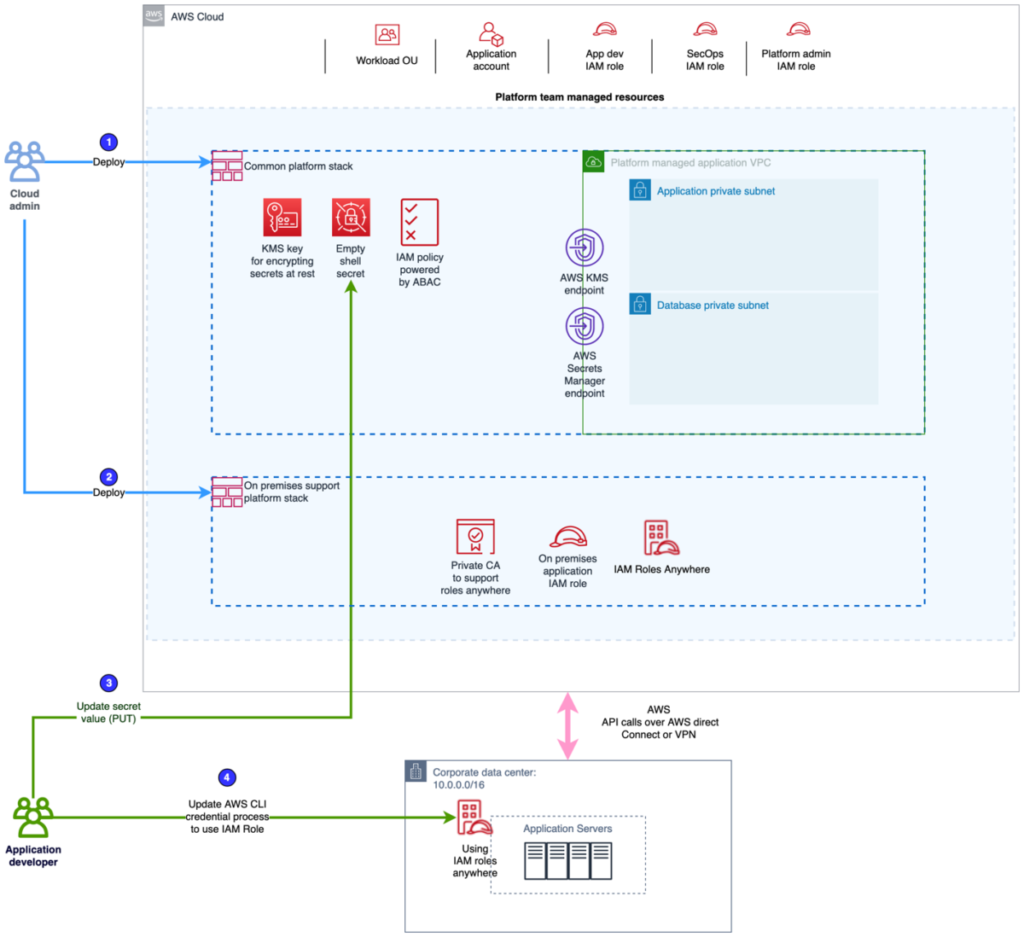
In Part 1 of this series, we provided guidance on how to discover and classify secrets and design a migration solution for customers who plan to migrate secrets to AWS Secrets Manager... In this post, we discuss how teams should approach the next phase, which is implementing the migration of secrets to Secrets Manager... Implement secrets migration Application teams lead the effort to design the...
In Part 1 of this series, we provided guidance on how to discover and classify secrets and design a migration solution for customers who plan to migrate secrets to AWS Secrets Manager... In this post, we discuss how teams should approach the next phase, which is implementing the migration of secrets to Secrets Manager... Implement secrets migration Application teams lead the effort to design the...
Migrating your secrets to AWS Secrets Manager, Part I: Discovery and design
TutoSartup excerpt from this article:
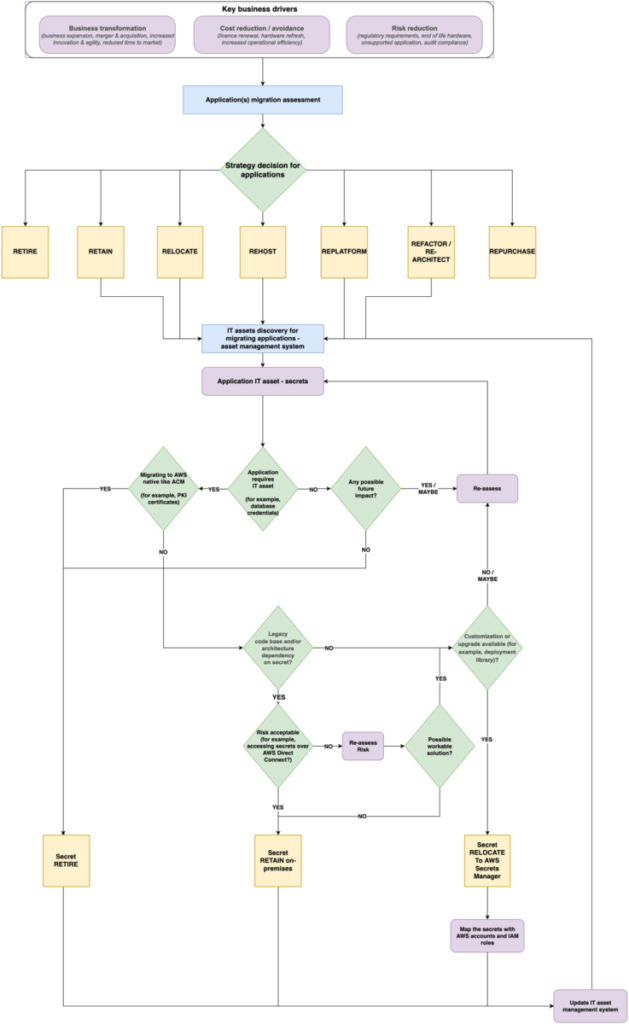
” – Benjamin Franklin A secret can be defined as sensitive information that is not intended to be known or disclosed to unauthorized individuals, entities, or processes... Secrets like API keys, passwords, and SSH keys provide access to confidential systems and resources, but it can be a challenge for organizations to maintain secure and consistent management of these secrets... Commonly obs...
” – Benjamin Franklin A secret can be defined as sensitive information that is not intended to be known or disclosed to unauthorized individuals, entities, or processes... Secrets like API keys, passwords, and SSH keys provide access to confidential systems and resources, but it can be a challenge for organizations to maintain secure and consistent management of these secrets... Commonly obs...
New training for c-suite builds awareness of cloud, generative AI capabilities
TutoSartup excerpt from this article:
The cloud powers today’s most impactful business and customer experiences, and c-suite leaders increasingly want to understand what it can deliver for their organization... Regardless of your organization’s adoption of cloud technologies, executives who understand the capabilities of cloud and its impact on operations across the organization are better equipped to set the vision for their orga...
The cloud powers today’s most impactful business and customer experiences, and c-suite leaders increasingly want to understand what it can deliver for their organization... Regardless of your organization’s adoption of cloud technologies, executives who understand the capabilities of cloud and its impact on operations across the organization are better equipped to set the vision for their orga...
Temporal data lake architecture for benchmark and indices analytics
TutoSartup excerpt from this article:
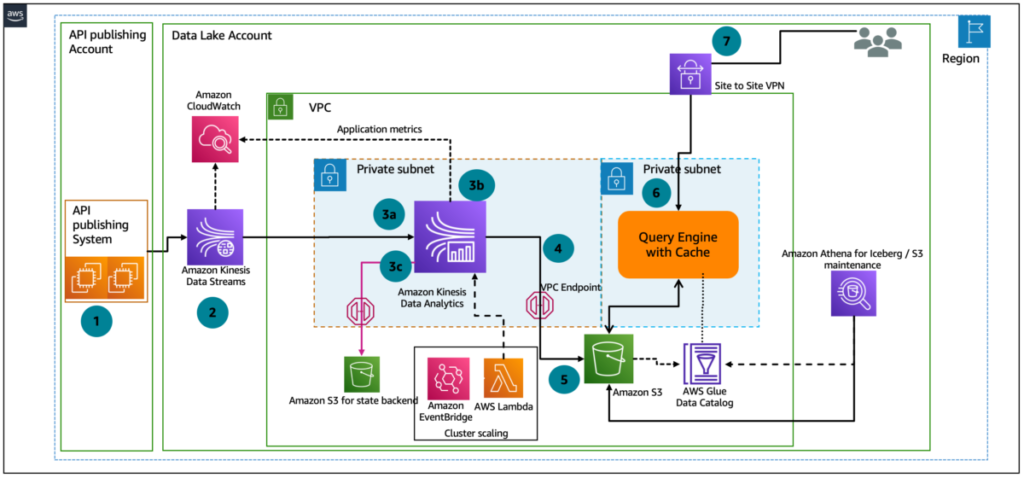
Achieving this requires a processing architecture that can handle large volumes of data during peak bursts, meet strict latency requirements, and scale according to incoming volumes... In this post, we’ll describe a scenario for an industry leader in the financial services sector and explain how AWS services are used for bi-temporal processing with state management and scale based on variable ...
Achieving this requires a processing architecture that can handle large volumes of data during peak bursts, meet strict latency requirements, and scale according to incoming volumes... In this post, we’ll describe a scenario for an industry leader in the financial services sector and explain how AWS services are used for bi-temporal processing with state management and scale based on variable ...

AWS re:Inforce 2023: Key announcements and session highlights
TutoSartup excerpt from this article:
The conference featured a lineup of over 250 engaging sessions and hands-on labs, in collaboration with more than 80 AWS partner sponsors, over two days of immersive cloud security learning... They shared the latest innovations in cloud security from AWS and provided insights on how to foster a culture of security in your organization... Amazon Inspector code scanning of Lambda functions scans cu...
The conference featured a lineup of over 250 engaging sessions and hands-on labs, in collaboration with more than 80 AWS partner sponsors, over two days of immersive cloud security learning... They shared the latest innovations in cloud security from AWS and provided insights on how to foster a culture of security in your organization... Amazon Inspector code scanning of Lambda functions scans cu...
