
SEC and Binance seek compromise on US assets freeze
TutoSartup excerpt from this article:
In the wake of the SEC’s lawsuit against Binance and Zhao, the commission filed an emergency request with the court to have BAM Trading’s assets frozen...US rebuts motion to freeze fundsBAM Trading responded by filing an opposition argument, which essentially stated that it was the belief of the company and its lawyers that the SEC’s underlying rationale for requesting the freeze didn’t me...
In the wake of the SEC’s lawsuit against Binance and Zhao, the commission filed an emergency request with the court to have BAM Trading’s assets frozen...US rebuts motion to freeze fundsBAM Trading responded by filing an opposition argument, which essentially stated that it was the belief of the company and its lawyers that the SEC’s underlying rationale for requesting the freeze didn’t me...

Reinventing the data experience: Use generative AI and modern data architecture to unlock insights
TutoSartup excerpt from this article:
The combination of large language models (LLMs), including the ease of integration that Amazon Bedrock offers, and a scalable, domain-oriented data infrastructure positions this as an intelligent method of tapping into the abundant information held in various analytics databases and data lakes... In the post, we showcase a scenario where a company has deployed a modern data architecture with dat...
The combination of large language models (LLMs), including the ease of integration that Amazon Bedrock offers, and a scalable, domain-oriented data infrastructure positions this as an intelligent method of tapping into the abundant information held in various analytics databases and data lakes... In the post, we showcase a scenario where a company has deployed a modern data architecture with dat...

How BrainPad fosters internal knowledge sharing with Amazon Kendra
TutoSartup excerpt from this article:
This post discusses how to structure internal knowledge sharing using Amazon Kendra and AWS Lambda and how Amazon Kendra solves the obstacles around knowledge sharing many companies face... We summarize BrainPad’s efforts in four key areas: What are the knowledge sharing problems that many companies face? Why did we choose Amazon Kendra? How did we implement the knowledge sharing syste...
This post discusses how to structure internal knowledge sharing using Amazon Kendra and AWS Lambda and how Amazon Kendra solves the obstacles around knowledge sharing many companies face... We summarize BrainPad’s efforts in four key areas: What are the knowledge sharing problems that many companies face? Why did we choose Amazon Kendra? How did we implement the knowledge sharing syste...
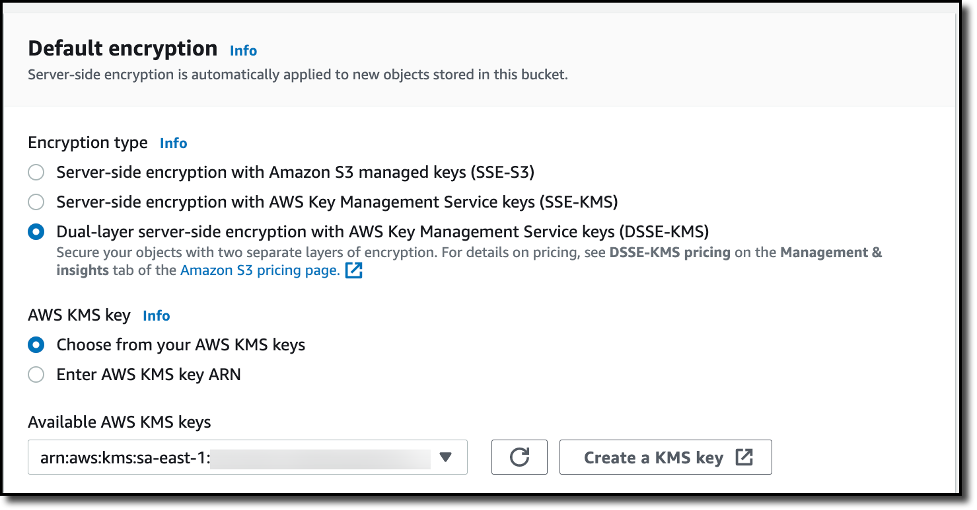
New – Amazon S3 Dual-Layer Server-Side Encryption with Keys Stored in AWS Key Management Service (DSSE-KMS)
TutoSartup excerpt from this article:
Today, we are launching Amazon S3 dual-layer server-side encryption with keys stored in AWS Key Management Service (DSSE-KMS), a new encryption option in Amazon S3 that applies two layers of encryption to objects when they are uploaded to an Amazon Simple Storage Service (Amazon S3) bucket...0 guidance for two layers of CNSA encryption... Using DSSE-KMS, you can fulfill regulatory requirements to ...
Today, we are launching Amazon S3 dual-layer server-side encryption with keys stored in AWS Key Management Service (DSSE-KMS), a new encryption option in Amazon S3 that applies two layers of encryption to objects when they are uploaded to an Amazon Simple Storage Service (Amazon S3) bucket...0 guidance for two layers of CNSA encryption... Using DSSE-KMS, you can fulfill regulatory requirements to ...
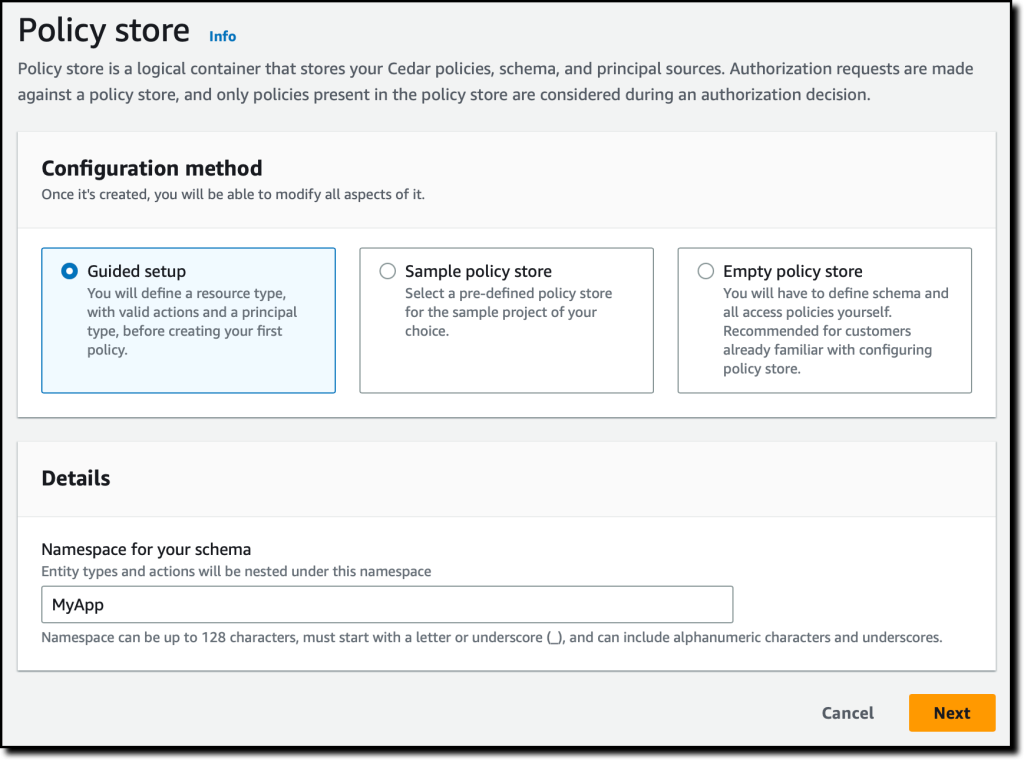
Simplify How You Manage Authorization in Your Applications with Amazon Verified Permissions – Now Generally Available
TutoSartup excerpt from this article:
Amazon Verified Permissions centralizes permissions in a policy store and helps developers use those permissions to authorize user actions within their applications... Similar to how an identity provider simplifies authentication, a policy store lets you manage authorization in a consistent and scalable way... To define fine-grained permissions, Amazon Verified Permissions uses Cedar, an open-so...
Amazon Verified Permissions centralizes permissions in a policy store and helps developers use those permissions to authorize user actions within their applications... Similar to how an identity provider simplifies authentication, a policy store lets you manage authorization in a consistent and scalable way... To define fine-grained permissions, Amazon Verified Permissions uses Cedar, an open-so...

Bitstamp now included on FCA’s list of registered crypto firms
TutoSartup excerpt from this article:
The Financial Conduct Authority listed 42 registered crypto firms in compliance with the U... The United Kingdom arm of cryptocurrency exchange Bitstamp has joined the list of registered firms under the country’s Financial Conduct Authority...According to the FCA list of registered crypto-asset firms as of June 13, Bitstamp U... The F...
The Financial Conduct Authority listed 42 registered crypto firms in compliance with the U... The United Kingdom arm of cryptocurrency exchange Bitstamp has joined the list of registered firms under the country’s Financial Conduct Authority...According to the FCA list of registered crypto-asset firms as of June 13, Bitstamp U... The F...

Post-quantum hybrid SFTP file transfers using AWS Transfer Family
TutoSartup excerpt from this article:
To help provide long-term protection of encrypted data, AWS has been introducing quantum-resistant key exchange in common transport protocols used by AWS customers... In this blog post, we introduce post-quantum hybrid key exchange with Kyber, the National Institute of Standards and Technology’s chosen quantum-resistant key encapsulation algorithm, in the Secure Shell (SSH) protocol... Why use...
To help provide long-term protection of encrypted data, AWS has been introducing quantum-resistant key exchange in common transport protocols used by AWS customers... In this blog post, we introduce post-quantum hybrid key exchange with Kyber, the National Institute of Standards and Technology’s chosen quantum-resistant key encapsulation algorithm, in the Secure Shell (SSH) protocol... Why use...
