
AWS Week in Review – AWS Notifications, Serverless event, and More – May 8, 2023
TutoSartup excerpt from this article:
Along with many customers and colleagues from AWS, we are going to be live on May 17 at a virtual free event... During the AWS Serverless Innovation Day we will share best practices related to building event-driven applications and using serverless functions and containers... Get a calendar reminder and check the full agenda at the event site... AWS Open-Source News and Updates – This is a ...
Along with many customers and colleagues from AWS, we are going to be live on May 17 at a virtual free event... During the AWS Serverless Innovation Day we will share best practices related to building event-driven applications and using serverless functions and containers... Get a calendar reminder and check the full agenda at the event site... AWS Open-Source News and Updates – This is a ...
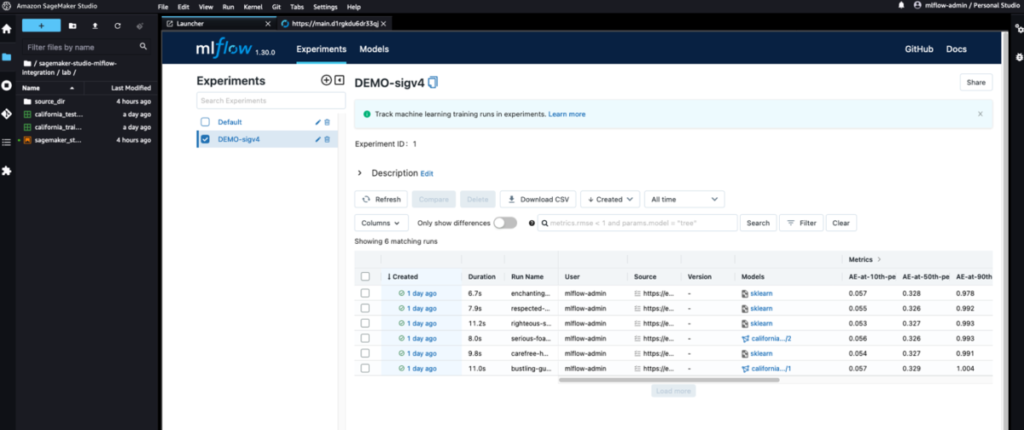
Securing MLflow in AWS: Fine-grained access control with AWS native services
TutoSartup excerpt from this article:
This post provides a solution tailored to customers that are already using MLflow, an open-source platform for managing ML workflows... In a previous post, we discussed MLflow and how it can run on AWS and be integrated with SageMaker—in particular, when tracking training jobs as experiments and deploying a model registered in MLflow to the SageMaker managed infrastructure... However, the open...
This post provides a solution tailored to customers that are already using MLflow, an open-source platform for managing ML workflows... In a previous post, we discussed MLflow and how it can run on AWS and be integrated with SageMaker—in particular, when tracking training jobs as experiments and deploying a model registered in MLflow to the SageMaker managed infrastructure... However, the open...
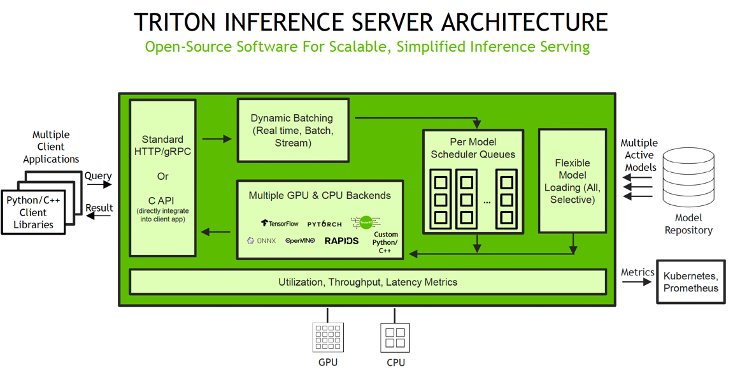
Host ML models on Amazon SageMaker using Triton: TensorRT models
TutoSartup excerpt from this article:
Sometimes it can be very beneficial to use tools such as compilers that can modify and compile your models for optimal inference performance... We explore how TensorRT works and how to host and optimize these models for performance and cost efficiency on SageMaker... SageMaker provides single model endpoints (SMEs), which allow you to deploy a single ML model, or multi-model endpoints (MMEs), whic...
Sometimes it can be very beneficial to use tools such as compilers that can modify and compile your models for optimal inference performance... We explore how TensorRT works and how to host and optimize these models for performance and cost efficiency on SageMaker... SageMaker provides single model endpoints (SMEs), which allow you to deploy a single ML model, or multi-model endpoints (MMEs), whic...
Insights from the 2023 Open Confidential Computing Conference
TutoSartup excerpt from this article:
This year's event was particularly noteworthy due to a panel discussion on the impact and future of confidential computing... Felix Schuster, Chief Executive Officer at Edgeless Systems, moderated the panel discussion, which explored topics such as the definition of confidential computing, customer adoption patterns, current challenges, and future developments...What is confidential compu...
This year's event was particularly noteworthy due to a panel discussion on the impact and future of confidential computing... Felix Schuster, Chief Executive Officer at Edgeless Systems, moderated the panel discussion, which explored topics such as the definition of confidential computing, customer adoption patterns, current challenges, and future developments...What is confidential compu...
Build an image search engine with Amazon Kendra and Amazon Rekognition
TutoSartup excerpt from this article:
In this post, we discuss a machine learning (ML) solution for complex image searches using Amazon Kendra and Amazon Rekognition... Specifically, we use the example of architecture diagrams for complex images due to their incorporation of numerous different visual icons and text... With the internet, searching and obtaining an image has never been easier... Most of the time, you can accurately loc...
In this post, we discuss a machine learning (ML) solution for complex image searches using Amazon Kendra and Amazon Rekognition... Specifically, we use the example of architecture diagrams for complex images due to their incorporation of numerous different visual icons and text... With the internet, searching and obtaining an image has never been easier... Most of the time, you can accurately loc...
Create high-quality datasets with Amazon SageMaker Ground Truth and FiftyOne
TutoSartup excerpt from this article:
In this post, we show how to repurpose an existing dataset via data cleaning, preprocessing, and pre-labeling with a zero-shot classification model in FiftyOne, and adjusting these labels with Amazon SageMaker Ground Truth... In the following sections, we demonstrate how to do the following: Visualize the dataset in FiftyOne Clean the dataset with filtering and image deduplication in Fifty...
In this post, we show how to repurpose an existing dataset via data cleaning, preprocessing, and pre-labeling with a zero-shot classification model in FiftyOne, and adjusting these labels with Amazon SageMaker Ground Truth... In the following sections, we demonstrate how to do the following: Visualize the dataset in FiftyOne Clean the dataset with filtering and image deduplication in Fifty...
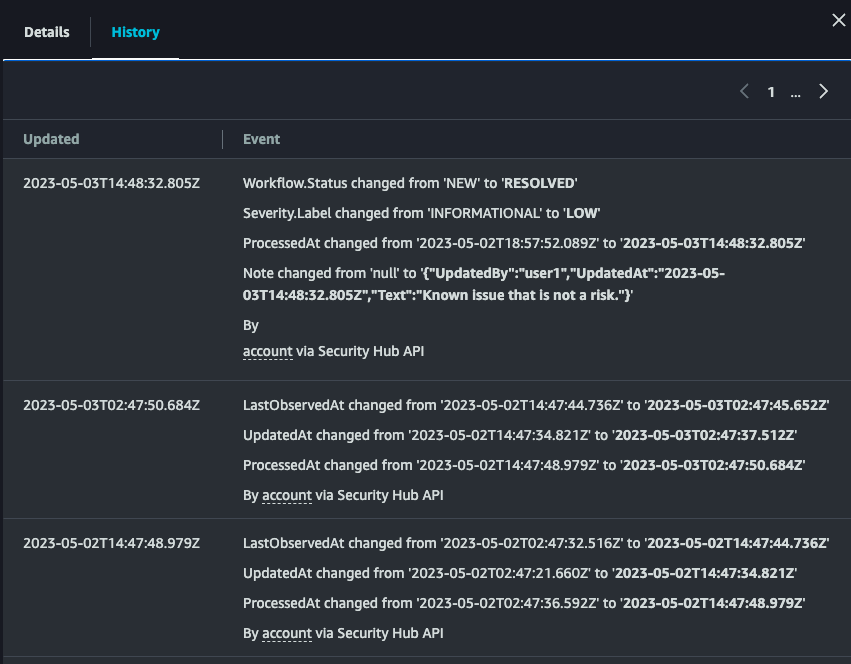
Get details on security finding changes with the new Finding History feature in Security Hub
TutoSartup excerpt from this article:
In today’s evolving security threat landscape, security teams increasingly require tools to detect and track security findings to protect their organizations’ assets... One objective of cloud security posture management is to identify and address security findings in a timely and effective manner... AWS Security Hub aggregates, organizes, and prioritizes security alerts and findings from vario...
In today’s evolving security threat landscape, security teams increasingly require tools to detect and track security findings to protect their organizations’ assets... One objective of cloud security posture management is to identify and address security findings in a timely and effective manner... AWS Security Hub aggregates, organizes, and prioritizes security alerts and findings from vario...
