Distributed training and efficient scaling with the Amazon SageMaker Model Parallel and Data Parallel Libraries
TutoSartup excerpt from this article:
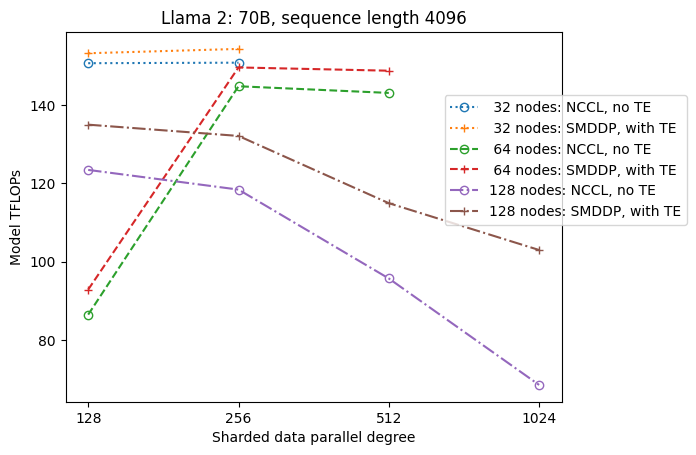
There has been tremendous progress in the field of distributed deep learning for large language models (LLMs), especially after the release of ChatGPT in December 2022... In December 2023, Amazon announced the release of the SageMaker model parallel library 2...0 (SMP), which achieves state-of-the-art efficiency in large model training, together with the SageMaker distributed data parallelism lib...
There has been tremendous progress in the field of distributed deep learning for large language models (LLMs), especially after the release of ChatGPT in December 2022... In December 2023, Amazon announced the release of the SageMaker model parallel library 2...0 (SMP), which achieves state-of-the-art efficiency in large model training, together with the SageMaker distributed data parallelism lib...
Manage your Amazon Lex bot via AWS CloudFormation templates
TutoSartup excerpt from this article:
Managing your Amazon Lex bots using AWS CloudFormation allows you to create templates defining the bot and all the AWS resources it depends on... The benefits of using CloudFormation include: Consistency – A CloudFormation template provides a more consistent and automated way to deploy and manage the resources associated with an Amazon Lex bot... Version control – With AWS CloudFormati...
Managing your Amazon Lex bots using AWS CloudFormation allows you to create templates defining the bot and all the AWS resources it depends on... The benefits of using CloudFormation include: Consistency – A CloudFormation template provides a more consistent and automated way to deploy and manage the resources associated with an Amazon Lex bot... Version control – With AWS CloudFormati...

A secure approach to generative AI with AWS
TutoSartup excerpt from this article:
Generative artificial intelligence (AI) is transforming the customer experience in industries across the globe... Customers are building generative AI applications using large language models (LLMs) and other foundation models (FMs), which enhance customer experiences, transform operations, improve employee productivity, and create new revenue channels... FMs and the applications built around t...
Generative artificial intelligence (AI) is transforming the customer experience in industries across the globe... Customers are building generative AI applications using large language models (LLMs) and other foundation models (FMs), which enhance customer experiences, transform operations, improve employee productivity, and create new revenue channels... FMs and the applications built around t...
Anthropic’s Claude 3 Opus model is now available on Amazon Bedrock
TutoSartup excerpt from this article:
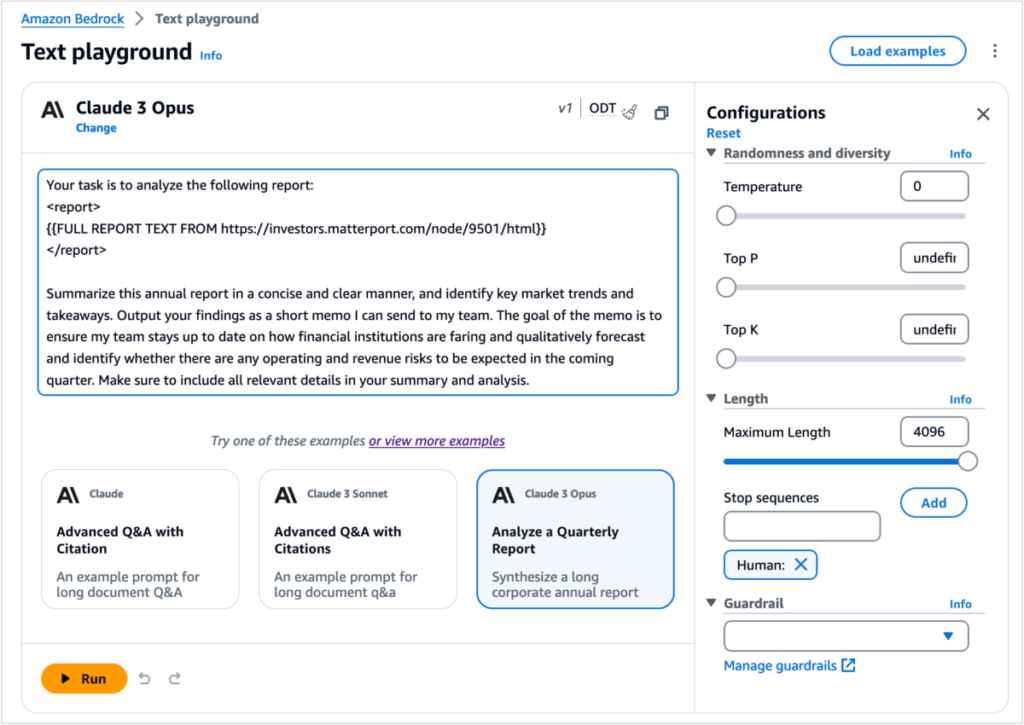
When Anthropic announced its Claude 3 foundation models (FMs) on March 4, we made Claude 3 Sonnet, a model balanced between skills and speed, available on Amazon Bedrock the same day... On March 13, we launched the Claude 3 Haiku model on Amazon Bedrock, the fastest and most compact member of the Claude 3 family for near-instant responsiveness... Today, we are announcing the availability of Anth...
When Anthropic announced its Claude 3 foundation models (FMs) on March 4, we made Claude 3 Sonnet, a model balanced between skills and speed, available on Amazon Bedrock the same day... On March 13, we launched the Claude 3 Haiku model on Amazon Bedrock, the fastest and most compact member of the Claude 3 family for near-instant responsiveness... Today, we are announcing the availability of Anth...
Where’s The Downside Tipping Point For US Stocks?
TutoSartup excerpt from this article:
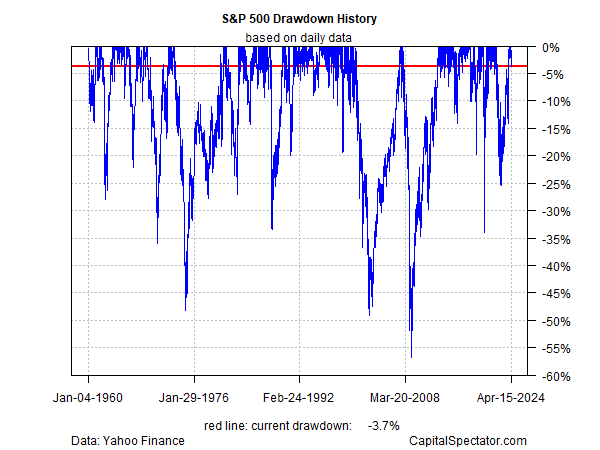
Yesterday’s sharp slide in US equities has refocused minds on a hardy perennial: the market can and does go down... Deciding whether the market’s latest gyrations are noise or signal is the art/science of market analysis... The market yesterday (Apr...7% below its previous peak – a drawdown that’s irrelevant in the grand scheme of market history for peak-to-trough declines... What would co...
Yesterday’s sharp slide in US equities has refocused minds on a hardy perennial: the market can and does go down... Deciding whether the market’s latest gyrations are noise or signal is the art/science of market analysis... The market yesterday (Apr...7% below its previous peak – a drawdown that’s irrelevant in the grand scheme of market history for peak-to-trough declines... What would co...
Macro Briefing: 16 April 2024
TutoSartup excerpt from this article:
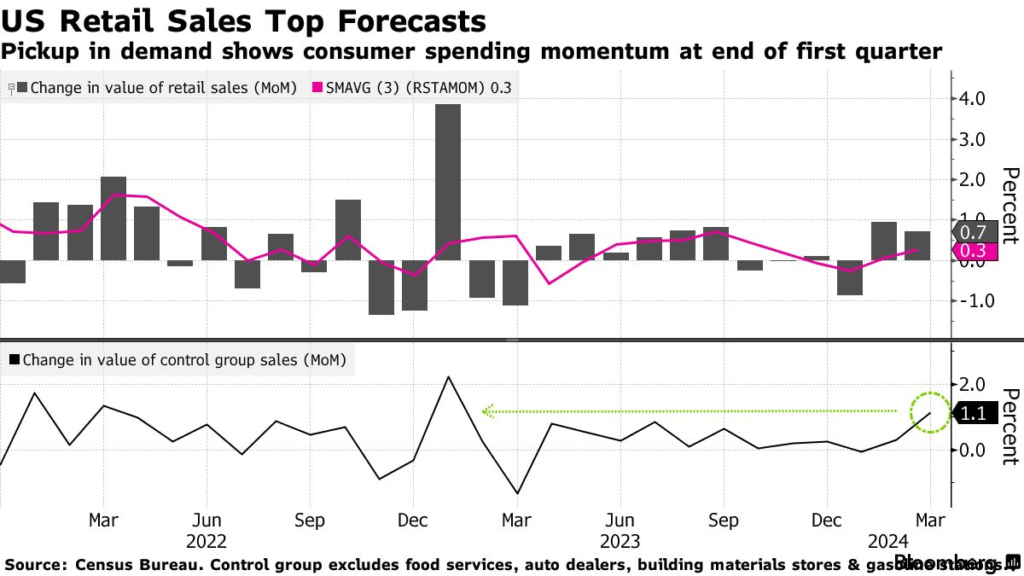
* Another round of Fed rate hikes is possible, advise UBS strategists * China’s economy grew faster than expected in Q1, but… * New home prices in China fall at fastest rate since 2015 * NY Fed Mfg Index continues to indicate contraction in April * US home builder sentiment steady at modest growth level in April * US retail sales rose more than forecast in March:Economists expect US economi...
* Another round of Fed rate hikes is possible, advise UBS strategists * China’s economy grew faster than expected in Q1, but… * New home prices in China fall at fastest rate since 2015 * NY Fed Mfg Index continues to indicate contraction in April * US home builder sentiment steady at modest growth level in April * US retail sales rose more than forecast in March:Economists expect US economi...
Congratulations to the PartyRock generative AI hackathon winners
TutoSartup excerpt from this article:
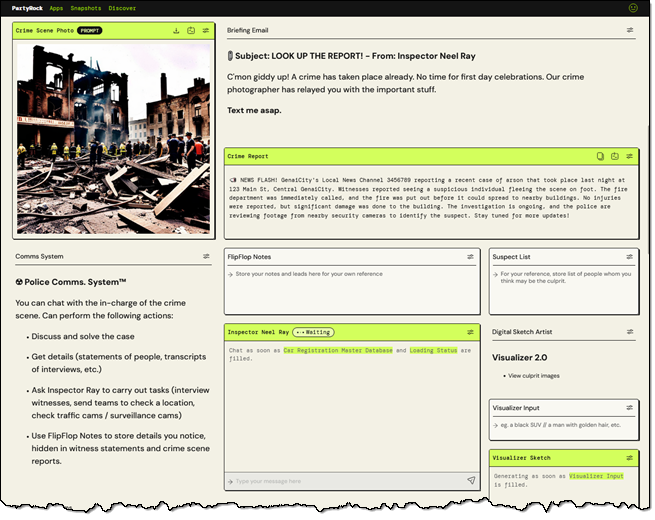
The hackathon attracted 7,650 registrants who submitted over 1,200 projects, and published over 250 project blog posts on community... To learn more, read the hackathon submission and the blog post... To learn more, read the hackathon submission... Great work, Michael! To learn more, read the hackathon submission... Let’s take a quick look at the winners of the top 3 prizes… First ...
The hackathon attracted 7,650 registrants who submitted over 1,200 projects, and published over 250 project blog posts on community... To learn more, read the hackathon submission and the blog post... To learn more, read the hackathon submission... Great work, Michael! To learn more, read the hackathon submission... Let’s take a quick look at the winners of the top 3 prizes… First ...
