
Transforming Maya’s API management with Amazon API Gateway
Security posture maintenance: While Maya maintained a strong security posture, doing so across the numerous independent gateways was unsustainable…In this post, you will learn how Amazon Web Services (AWS) customer, Maya, the Philippines’ leading fintech company and digital bank, built an API…
In this post, you will learn how Amazon Web Services (AWS) customer, Maya, the Philippines’ leading fintech company and digital bank, built an API management platform to address the growing complexities of managing multiple APIs hosted on Amazon API Gateway. API Gateway is a fully managed service that you can use to create RESTful and WebSocket APIs.
At Maya, different teams build APIs to expose their services to merchants. As the number of applications grew, the overhead of managing APIs increased. An API platform is a set of tools to simplify and standardize across API management concerns such as security, governance, automated deployments, observability, and integrations with multiple AWS accounts. This frees up application teams to focus on features while offloading management concerns to the API platform.
Initial state
Prior to implementing the API platform, Maya used a decentralized API management approach, which created significant challenges. Individual teams operated independent API gateways, resulting in fragmented infrastructure, leading to several issues:
- Lack of standardization: Implementing consistent API standards across the organization proved difficult. Each team maintained its own configurations and practices, leading to inconsistencies in security and documentation.
- Security posture maintenance: While Maya maintained a strong security posture, doing so across the numerous independent gateways was unsustainable. The overhead of applying consistent security policies and updates across all gateways was becoming increasingly burdensome.
- Inconsistent operational visibility: Observability wasn’t inherently limited, rather inconsistently applied. Having multiple, different gateways makes it challenging to enforce a unified observability strategy and correlate data across the entire API ecosystem.
Solution overview
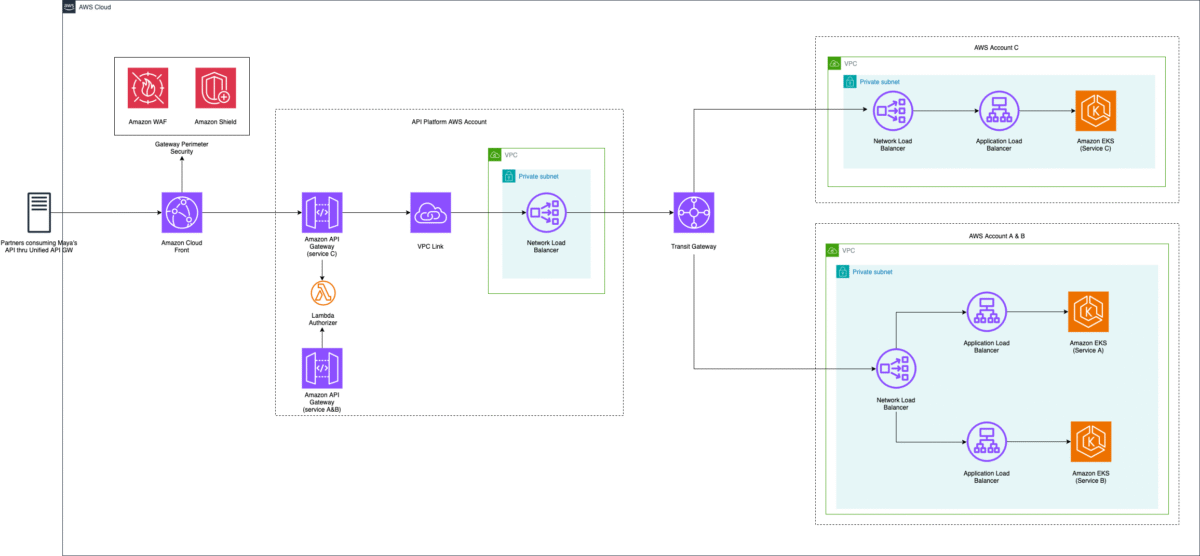
To address these challenges, Maya implemented an API platform, code-named Unified API Gateway. This centralized API management helps enforce consistent standards and improve overall security and observability. The following image illustrates the architecture of the Unified API Gateway and how it integrates with backend services managed and owned by different teams across different AWS accounts.

API Platform Architecture
Maya chose to host all APIs in a central API account to centralize governance. This is managed by a dedicated shared services cloud team. Amazon CloudFront with AWS WAF and AWS Shield Advanced integration provides perimeter security. An AWS Lambda authorizer provides application security by managing authentication, authorization, and session management. This mitigates against the OWASP top 10 API security risks.
Integration to backend services is configured through API Gateway private integration and AWS Transit Gateway. In a decentralized API deployment strategy where APIs are co-hosted with the service in the respective AWS account, the integration will be simpler because you won’t need cross-account network connectivity. You will still benefit from the API management techniques covered in this post.
Standardization through structured service on-boarding
OpenAPI Specification (OAS) provides a structured definition for APIs. As shown in the following figure, service teams define the API OAS specification. This is embedded in Terraform infrastructure-as-code template for API Gateway. These are checked into source code repository and deployed using GitLab CI.

API Gateway Infrastructure-as-code (IaC) Pipeline
A configuration file used as a Terraform template supplies parameters for components of the solution such as backend integration, Lambda authorizer details, and additional headers for auditing. The following OAS snippets demonstrate this.
- Integration with the backend service
x-amazon-apigateway-integration: type: "http_proxy" connectionId: "${vpc_link_id}" httpMethod: "GET" uri: "http://$${stageVariables.url}:11620/v1/api/endpoint/{id}" # double $ is not a typo - Adding headers to the request
x-amazon-apigateway-integration: type: "http_proxy" connectionId: "${vpc_link_id}" httpMethod: "GET" uri: "http://$${stageVariables.url}:11620/v1/api/endpoint/{id}" requestParameters: integration.request.header.x-requesting-service-id: "'api-gw'" integration.request.header.x-org-customer-id: "context.authorizer.x-org-customer-id" - Security definition
securitySchemes: lambda-authorizer: type: "${authorizer_type}" name: "${authorizer_name}" x-amazon-apigateway-authtype: "custom" x-amazon-apigateway-authorizer: type: "request" authorizerUri: "${authorizer_uri}" authorizerCredentials: "${authorizer_credentials}" identitySource: "${authorizer_identity_source}"
API Gateway supports most of the OpenAPI 2.0 specification and the OpenAPI 3.0 specification but there are a few exceptions. Maya uses a custom plugin in the pipeline to enforce necessary limiting rules to help ensure compatibility with API Gateway.
To simplify deployment for development teams, a custom Terraform module abstracts away the API Gateway implementation details.
module "test-microservice-api-gateway" {
# module version parameters
source = "gitlabinstance.com/platform-engineering/apigw-terraform-module/aws"
version = "1.2.7"
# module deployed infrastructure parameters
api_name = var.api_name
api_mapping_path = var.api_mapping_path
environment = var.environment
aws_region = var.aws_region
account_id = var.account_id
tags = var.tags
domain_name = var.domain_name
stage_name = var.stage_name
oas_path = var.oas_path # this value is populated via environment variable in Gitlab CI/CD
providers = {
aws = aws.apigw
}
authorizer_credentials = var.authorizer_credentials
authorizer_uri = var.authorizer_uri
vpc_link_id = var.vpc_link_id
endpoint_url = var.endpoint_url
}To use multi-level prefixes for custom domains with REST API Gateway, you need the Terraform module for API Gateway v2.
resource "aws_api_gateway_rest_api" "apigw" {
name = "${var.environment}-${var.api_name}"
body = templatefile(
local.oasFilePath,
{
vpc_link_id = var.vpc_link_id
authorizer_uri = var.authorizer_uri
authorizer_credentials = var.authorizer_credentials
}
)
description = "API Gateway for ${var.api_name}"
endpoint_configuration {
types = ["REGIONAL"]
}
# Default endpoint needs to be disabled if CloudFront is used as entry point to API Gateway
disable_execute_api_endpoint = true
tags = local.tags
}
# Use apigatewayv2 in order to have multi level base path ex. /v1/service_name
resource "aws_apigatewayv2_api_mapping" "this" {
domain_name = var.domain_name
api_id = aws_api_gateway_rest_api.apigw.id
stage = aws_api_gateway_stage.apigw.stage_name
api_mapping_key = var.api_mapping_path
}Simplify API security with automation
Maya’s Unified API Gateway implements a robust, multi-layered security strategy. This approach helps ensure comprehensive protection from external threats and enforces stringent access control policies.
AWS WAF inspects and filters incoming traffic to protect against common web exploits, including OWASP Top 10, such as SQL injection and cross-site scripting attacks. A combination of custom and managed rule sets blocks malicious requests and enforces security policies. AWS Shield Advanced mitigates distributed denial of service (DDoS) attacks and provides 24/7 access to the AWS Shield Response Team (SRT) for expert support during attack events. This helps ensure high availability and resiliency.
API Gateway is integrated with a Lambda authorizer for authentication and authorization. The custom function implements fine-grained access control based on several factors such as identity, roles, and scopes.
To help ensure the consistency and integrity of the API configurations, all updates and deployments are strictly managed through an automated infrastructure-as-code (IaC) pipeline. This helps eliminate the risk of unauthorized or accidental manual changes to the API Gateway and any underlying infrastructure. The IaC pipeline makes sure that all API configurations, including security settings, are deployed through a controlled and auditable process. This prevents configuration drift and makes sure that security policies are consistently applied across all APIs. This also means that all changes are subject to code reviews and version control, adding another layer of security and traceability.
End-to-end visibility with observability
Maya’s Unified API Gateway prioritizes comprehensive observability to proactively monitor API performance, identify potential issues, and provide a seamless user experience. It uses a combination of AWS services and integrated tools to achieve this.
Amazon CloudWatch is used to monitor key performance metrics, including latency, error rates, and requests counts. CloudWatch provides real-time insights into the health and performance of APIs. Alerts on P95 and P99 values help identify and address performance bottlenecks, ensuring responsiveness.
CloudWatch metrics are streamed to Dynatrace, an application performance monitoring (APM) tool. The centralized view helps correlate data from various sources, create custom dashboards, and configure intelligent alerts based on predefined thresholds.
To help ensure complete visibility into API activity, the Lambda authorizer and API Gateway access logs are centralized in Splunk. This provides a comprehensive audit trail to track authentication and authorization events, identify security incidents, and troubleshoot API requests. Headers generated after authentication and authorization are done are passed down to the backend services for proper log correlation.
Future roadmap
The Unified API Gateway will continue to evolve to meet the growing needs of the organization and its partners and customers. The following are the key future enhancements that will further streamline API management, improve the developer experience, and enhance security.
- Integration with the internal developer portal: This will provide a self-service UI for bootstrapping new APIs from scratch and further empower developers. This will also simplify documentation and discovery by cataloging all APIs
- A modular, extension-based design for enhanced processing: This will introduce custom processing of requests in-line in the gateway account before integrating with backend services. Examples include digital signature verification, message transformation, and custom business logic. A modular design will offer a flexible and scalable way to enhance the functionality of Maya’s APIs without modifying backend services.
- Bring your own (BYO) authorizer: Support a wider range of identity providers and authentication protocols, providing greater flexibility and control over API access.
- Centralizing schema validation: Moving schema validation to API Gateway to bring consistency and improve the robustness and security of APIs by preventing malformed or malicious requests from being processed.
- API monetization: Create new revenue streams by adding support for usage-based billing, tiered pricing, and subscription models.
Conclusion
This post has described the creation of Maya’s robust API management and governance solution, using a combination of native AWS services and powerful partner tools such as Terraform and Dynatrace. We’ve demonstrated how this Unified API Gateway has streamlined and automated core API processes, transforming Maya’s previously fragmented infrastructure into a secure and observable ecosystem. By establishing clear guardrails, the API solution team empowers developers to rapidly deploy APIs while maintaining consistent standards.
With the recent implementation of this solution across more teams, Maya is focused on defining and tracking key performance indicators (KPIs). We anticipate measuring critical metrics such as API onboarding efficiency, developer experience, API latency, and security incident rates. These insights will serve as a foundation for continuous improvement and optimization, ensuring the solution’s sustained effectiveness and evolution.
Visit the API platform guidance on Serverlessland to learn more about building API platforms. See the API Gateway pattern collection to learn more about designing REST API integrations on AWS.
About the Authors
Author: Arthi Jaganathan
